Best Authentication Software for Small Medium Enterprises
The process of confirming that someone is, in fact, who they claim to be, is known as authentication. Some of the Best Authentication Software For Small Medium Enterprises
Employing the best authentication software ensures comparing a user's credentials to those stored in a database of authorized users or on a data authentication server.
Authentication ensures safe systems, secure business processes, and secure corporate data. By limiting access to protected resources to only authorized users or processes, authentication helps companies maintain the security of their networks.
What Is Authentication Software?
Authentication Software maintains identification information or simply speaking data allowing to identify a person, such as a username, password, and other necessary information. Rather than using a physical device, authentication software allows individuals to be verified using a desktop or mobile application. Other names for this are phone-as-a-token authentication, soft token authentication, and mobile authentication. While you log into your account, whether on a desktop, mobile device, or when you're doing a financial transaction, authentication software is used to verify your identity.
Why Is User Authentication Important?
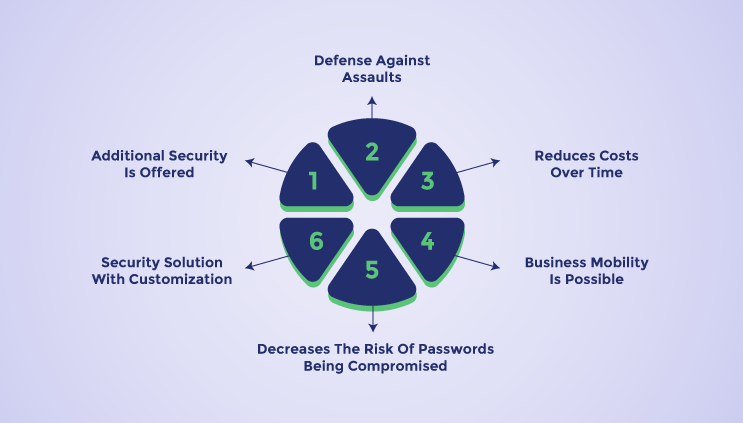
The most important thing most businesses can do to avoid cybersecurity issues is to implement a good multi factor authentication. Governments are taking cybersecurity more seriously as agencies and infrastructure are being targeted, even in sectors where authentication is not currently required for regulatory compliance. Investing in the best authentication software solution is a good method to safeguard your resources and secure your data from illegal access. A robust authentication software ensures the following:
Enhances The User Experience
Password resets are a common problem for IT teams in businesses that enforce strict password restrictions. Security is ensured via multi factor authentication without the need for time-consuming resets or complex rules. Additional Security Is Offered Since many people use the exact same passwords across several accounts, identity theft is simple to accomplish. By adding an additional layer of protection, password management software makes it more difficult for hackers to access users' accounts.
Defense Against Assaults
Hackers typically use brute force attacks to try to guess encryption keys or passwords. These, however, won't function if the login process requires an additional step. Hackers are stopped from breaking into your network using stolen passwords, devices, or other isolated pieces of information by forcing users to submit multiple credentials before accessing accounts.
Reduces Costs Over Time
A multi factor authentication system's initial setup may be expensive. The expenses of a security breach, which increase in likelihood without multi-factor authentication, are far higher. Decreases The Risk Of Passwords Being Compromised Passwords are the least secure type of authentication even though they are used most often. Passwords can be stolen or guessed, reused, or shared by users, putting account holders and system administrators at risk.
Security Solution With Customization
Every authentication method has a variety of choices, allowing businesses to tailor the user experience to their own requirements. Users can have access to fingerprint scanners on their devices, but not to voice recognition or retinal scanners, for instance. For some use cases, just two factors could be necessary, while other use cases might call for all three authentication elements.
Business Mobility Is Possible
Productivity is increased when employees can utilize mobile devices to quickly and securely access the resources they require. When combined with SSO, using multi-authentication software to enter into work apps gives employees the 24/7 access and flexibility they want while protecting networks and data.
Common Authentication Types
We'll now discuss the most popular authentication techniques available:
Password authentication: The most fundamental kind of password management is passwords, which are familiar to everybody who uses the internet.
Two-factor authentication (2FA): Users must cross a third barrier to log in after inputting their username and password. They must enter a one-time code from a specific physical device. The code may be produced via a mobile app or given to their phone through text message.
Token authentication: The 2FA in token systems is performed via a special physical device. This might be a USB dongle or smart card with a radio frequency identification or near-field communication chip that is plugged into the computer's USB port.
Biometric authentication: Biometrics use a user's bodily traits to identify them. The most extensively used biometric technologies are voice recognition, facial detection, iris or retinal scanning, fingerprints, and face recognition.
Transaction authentication: Compared to previous online authentication techniques, transaction authentication follows a distinct methodology. Instead of depending on the user's knowledge, it compares the user's traits with what it already knows about the user, looking for inconsistencies.
Computer recognition authentication: When a user initially logs in to these systems, a little software plug-in is installed on their computer. There is a cryptographic device marker in the plug-in. The marker is verified the following time the user signs in to make sure they are using the recognized device.
CAPTCHAs: This authentication approach looks to ascertain if a user is indeed human rather than confirming a specific user.
Single Sign-On (SSO): A significant aspect to take into account when selecting a device authentication mechanism is single login. A user may access numerous apps by entering their credentials just once, thanks to SSO.
Best Authentication Software For Small Medium Enterprises
By asking users to verify their identity in two or more ways before giving access to accounts, sensitive data, systems, or applications, multi factor authentication (MFA) software secures users' accounts. Users are asked for a second authentication factor in addition to a single authentication factor, such as entering a username and password, to confirm that they are who they say they are. Best verification software includes authentication factors like one-time passcodes (OTPs) for SMS, emails, and phone calls, software tokens, hardware tokens, biometric factors, and contextual or risk-based authentication. Following is the list of top 5 authentication softwares:
1. NinjaAuth
NinjaAuth provides customers a simple, safe method to log in to all of their accounts with only one username and password. This high degree of security helps to safeguard client data. NinjaAuth is one of the best enterprise authentication software for SSO authentication that is simple and user-friendly and works with many different hardware and operating systems. It provides developers with a centralized user interface where they can easy management of SSO access for numerous apps and view their allocated roles.
Top Features include:
Easy Management: It provides developers with a centralized user interface where they can manage SSO access for several apps and view their allocated roles.
Easy Setup: In a matter of minutes, configure SSO for your website or application. Simply adhere to the directions and upload the given code to your website or application.
Multi-factor Authentication: It ensures an additional degree of protection is added to prevent unauthorized people from accessing sensitive data.
Single Login: With a single click, a user may sign in to several apps using a Single Sign On Solution (SSO). Since users only need to input their credentials once, security is increased while saving time.
Playground: The app enables the creation of test accounts for developers so they may practice using the SSO API's different functionalities without compromising their actual account.
Access Controls: Your information may be protected in a more secure manner thanks to the access controls feature of single sign-on. Users can specify who has access to information and what actions they are permitted to take using this approach.
Secure Login: Instead of having to remember several usernames and passwords, users may log in to websites and applications using their credentials. Using a secure login system with two-factor authentication, unauthorized access is stopped.
Price: 39 Apps for one price of only $999
2. ADSelfService Plus
An on-premises access control system called ADSelfService Plus serves companies in a variety of sectors, including IT, finance, engineering, education, aviation, and telecommunications.
Key Features include:
Account unlocks, and self-service password resets: Users can use a web browser to change their AD passwords and unlock their domain accounts.
MFA: MFA may be used to protect cloud app logins, VPN and OWA logins, and machine logins.
Password synchronizer and SSO: Through SSO and real-time password synchronization, users may sign in to several apps using a single, unified identity.
Password policy enforcer: Administrators can set up unique password rules to compel the use of strong passwords.
Password expiration notifier: Admins can send email or SMS notifications to end users when their passwords are about to expire.
Price: On Request
3. Routee
A cloud-based platform called Routee was created to assist companies of all sizes in managing the whole SMS marketing workflow, from developing campaigns to producing leads. Bulk messaging, two-factor authentication, push alerts, real-time reporting, and analytics are some of the key features. It further allows Two-Factor Authentication with Fallback, SMS, Voice, Viber, and missed calls.
Create, automate, and manage your processes in a completely event-based environment. Set up channels and situations in priority order to maximize involvement. Through our portal, take complete control of all contextual communication and take pleasure in a smooth engagement with your company.
Customer activity may be observed and evaluated in real-time in detail, including time, location, messages read, and conversion rates. Deliver your messages simultaneously through several mediums.
Price: Based on Service Opted
4. Trusona
Trusona is a pioneer in passwordless MFA solutions for businesses in the media, healthcare, higher education, and financial services sectors. By offering a full authentication alternative to usernames and passwords, the company's workforce solutions make authentication more easy and safe.
Key Features include:
Full-stack authentication Workforce identity proofing Passwordless MFA Cascading MFA trust to SSO Workforce Identity Proofing, MFA for SSO, MFA with ID scanning passwordless and desktop MFA Price: Custom
5. DigitalPersona
An identity access management tool called DigitalPersona provides a variety of authentication techniques, such as one-time passwords, smartcards, biometrics, mobile-based push, and more. Businesses may use DigitalPersona to get passwords by responding to particular, predetermined questions and to have passwords automatically filled in for app access fields. The software further enables teams to create reports and gather information about user activity on a centralized dashboard.
Key features include:
It allows for app integration utilizing OpenID Connect or WS-Fed protocols when deployed on a server running Windows Active Directory, Azure Active Directory, or LDS.
The software has an intuitive UI that makes it simple to self-enroll credentials and enforce authentication policies.
It enables access to apps using OpenID Connect or WS-Fed through a browser-based SSO portal.
It provides a Password Manager function that is optional, which randomly generates and fills in passwords for login fields.
It supports FIDO2 authenticators that adhere to industry standards, including the YubiKey®, HID Crescendo® USB-A, and USB-C keys, and the HID Crescendo® C2300 smart card.
For your ADFS deployment, the DigitalPersona ADFS Extension offers a multi-factor authentication approach that includes biometric authentication using your face and fingerprint.
Price: On Request
Summing It Up
Best authentication softwares should provide two-factor authentication for extra shields to users from phishing, social engineering, and password assaults and stops logins from intruders using stolen or shoddy credentials. Since many people use the very same passwords across several accounts, identity theft is simple to accomplish. By adding an additional layer of protection, multi factor authentication makes it more difficult for hackers to access users' accounts.
NinjaAuth is radically altering how customers and employees log in. To provide consumers with the most reliable and seamless authentication available, 500apps’ NinjAuth has done away with passwords and any other factors that may be compromised. Check the website today for information!
Know Why NinjaAuth is the Best for Single Sign-On Solution?
Join the SaaS Revolution
-
All-in-One Suite of 50 apps
-
Unbelievable pricing - â¹999/user
-
24/5 Chat, Phone and Email Support
Infinity Suite
Tags
Email Finder Author Finder Email Validator Email List Email Hunter Email Checker Email Lookup Email Extractor Email Address Finder Email Scraper Find Emails CRM Software CRM Sales CRM CRM Software Enterprise CRM Software Cloud CRM Software Sales Enablement Workflow Automation Retail CRM Call Center CRM Real Estate CRM Sales Tool SDR Software Sales Engagement Platform Sales Qualified Leads Lead Management Tool Sales Tracking Sales Automation Outbound Sales Sales Prospecting Follow Up Leads Lead Management Call Center Software Call Center Software Outbound Call Center Auto Dialer Software Dialer Call Monitoring Automatic Call Distributor Answering Machine Detection Cloud Contact Center Software Virtual Call Center Call Management Time Tracking Time Tracking Employee Monitoring Time Tracker Time Tracking Software Timesheet Employee Time Clock Employee Tracking App Timekeeping Tracking App Time Clock App Applicant Tracking System ATS Applicant Tracking System Application Tracking System Applicant Software Recruiting Software ATS System Applicant Tracking Applicant Tracker Recruitment Software Candidate Relationship Management Systems Video Interviews Assessment Management Recruitment Software Video Interview Virtual Interview Coding Interview Interview Tool Online Assessment Employment Assessment Test Position Management Hiring App HRMS Software Human Resource Management HRMS Software HR Software Payroll Software Human Resource Software Employee Onboarding HRMS HR System Employee Management Document Management AI Writer Lead Enrichment AI Email Writer Sales Pitch Writer AI LinkedIn Outreach SEO Email writer Backlink Email Writer LinkedIn Chrome Extension Opening Line Writer Lead Generation Linkedin Search Prospect Lead Generation Sales Generation Data Enrichment CRM Integrations Technology Search Search with Email Integrations Website Search OKR Tool KPI OKR Task Management Performance Review Employee Performance Evaluation Employee Review Performance Management System OKR Goals MBO Email Notifications Learning Management System LMS Elearning Enterprise Learning Management Professional Development Employee Training Learning Management System Learning Platform Asynchronous Learning Training Management Knowledge Management Chatbot Chatbot AI Chatbot Customer Service Chatbot Online Chatbot Create Chatbot Messenger Chatbot Chatbot Software Website Chatbot Software Survey Bot Bot Builder Help Desk Software Ticketing Tool User Experience Help Desk Software Ticketing System Helpdesk Ticketing System Feedback Management Service Desk Software Support Ticketing Software Helpdesk Support Software Customer Service Ticketing System Live Chat Customer Service Software Live Chat Software Live Chat App Live Chat System Website Live Chat Live Chat Tool Web Chat Software Live Chat Support Software Customer Service Tool Live Chat Service Customer Feedback Customer Feedback Survey Customer Feedback Management Software Feedback Management Tool Customer Satisfaction Survey Software Customer Feedback Management System Client Feedback Software Survey Analysis Feedback Survey Software Feedback Management System User Feedback Software Customer Onboarding Customer Success Management Onboarding Process Workflows Customer Retention Customer Journey Onboarding Checklist User Segmentation Personalization Customized Templates Popup Builder API Platform End To End API Management Unified API Control REST API Management Web API Gateway API Documentation API Management API Integration API Development Unlimited Projects API Gateway Single Sign on Authentication Software Application Management Password Management SSO Configuration SSO Single Sign-On Access Management Easy Set-Up Single Login Secure Login App Builder App Builder Platform Low Code Application Platforms Low Code Development Build Your Own App Low Code App Software Drag And Drop Builder Custom Application Low Code Platform Low Code No Code Bespoke Software App Widgets Custom Widget File Picker Playground OAuth Keys File Manager Website Monitoring Reporting Web Application Monitoring Website Monitoring App Monitoring Performance Monitor App Baseline Analysis Location Insights Alerting System Reporting Wireframe Tool Design UI UX Project Management Mock Designer Wireframe Designer Website Mockup UI Prototyping Image Library Project Management Real-Time Updates Design UI UX Website Builder Website Builder Webpage Builder Website Creator Landing Page Creator Website Maker Blog Builder Ecommerce Website Builder Website Analytics Website Development Landing Page Builder Email Marketing Email Marketing Software Bulk Email Sender Automated Email Email Campaign Systems Email Automation Software Autoresponders Email Blast Service Email Marketing Email Marketing Automation Drip Campaigns Social Media Management Instagram Post Scheduler Social Media Analytics Social Media Management Social Media Planner Social Media Calendar Social Media Scheduling Social Media Listening Social Media Monitoring Social Listening SEO Tool Keyword Tool Link Building SEO Optimizer Website Audit On-Page SEO Broken Link Checker Rank Tracker Website Grader SEO Competitor Analysis Website Recording Website Analytics Click Tracking Usability Testing Website Monitoring Mouse Tracking Visitor Recording Session Replay Conversion Funnels Website Recording Website Visitor Tracker Website Personalization Lead Generation Tool Popup Maker Lead Generation Software Popup Builder Website Personalization Software Lead Capture Software Popup Builder Lead Capture Tool Lead Generation App Website Personalization App Content Planner Content Planner AI Writer Social Media Content Planner Ai Content Writer Social Media Content Calendar Content Generator AI Blog Writer Content Marketing Software Social Media Calendar Social Media Planner Push Notification Push Notification Push Messages Push Notification Service Push Service Push Notification App Custom Notifications Mobile Push Notifications Push Notification For Website Push Notification Tool Push Notification Providers Image Personalization Email Marketing Template Countdown Clock Personalization Software Personalized Software Countdown Clock Countdown Timer In Email Personalization Tool Personalized Images Personalized Videos Conversational Chatbot PPC Management Keyword Research PPC Management PPC Marketing Keyword Finder Keyword Generator Shopping Ads Adwords Reports Keyword Research Tool Keyword Suggestion Tool Team Chat Team Chat Software Collaboration Software Team Collaboration Team Communication Online Collaboration Collaboration Tool Teamwork Collaboration Virtual Communication Team Collaboration Software Business Phone System Virtual Phone Numbers Virtual PBX Toll Free Numbers Business Phone System IVR PBX Small Business Phone System PBX System VoIP Phone Cloud Phone Video Conferencing Video Conferencing Video Call Recording Virtual Conferencing Software Virtual Meetings Virtual Meeting Platforms Virtual Conference Platforms Online Conference Platforms Video Calling Software Cloud Meetings Video Conferencing Software Email Provider Email Software Software For Emails Hosted Emails Email With Domain Custom Email Address Email Hosting Business Email Address Email Encrypted Custom Domain Email Project Management Software Project Management Task Management Project Planner Project Management Tool Task Management Software Project Planning Software Project Management App Task Management App Project Management System Project Management Software Form Builder Form Builder Survey Builder Order Forms Web Forms Form Maker Form Creator Form Designer Survey Maker Survey Creator Custom Form Appointment Scheduling Appointment Scheduling Software Appointment Scheduling System Meetings Scheduler Appointment Scheduling App Online Appointment Scheduling Online Scheduling App Appointment Scheduler Appointment Booking App Calendar Scheduler Online Scheduler Robotic Process Automation RPA Tools RPA RPA Automation Robotic Automation Software Data Scraper Web Scraper Robotic Automation Website Scraper Business Process Automation Robotic Process Automation Business Process Management Workflow Management Business Process Modelling Business Process Automation BPMN BPM Software BPM Tool Business Process Management Workflow Software Workflow Automation Business Process Mapping App Integration Workflow Software Workflow App Workflow Automation Process Automation Application Integration Data Integration Tool Workflow Management Software Data Integration Software Workflow Tool Marketing Automation Electronic Signature Signature Maker Digital Signature Software Digital Signature Pdf Signer Esign Online Signature Signature Creator Sign Documents Online Electronic Sign E Signature
