What Are Multi Factor Authentication Work Types?
Security processes that require more than one identification method to verify the user's identity are supported by Multi Factor Authentication work types.

Traditional passwords are no longer safe enough. Hackers have devised various techniques for collecting passwords and gaining unauthorized access to private accounts, ranging from basic relaying and spraying assaults to the more complex dangers of spear-phishing and pharming. Microsoft engineers stated in March of this year that 99.9 percent of the account breach situations they deal with could have been prevented with multi factor authentication (MFA) solution.
What Is Multifactor Authentication?
MFA is an authentication mechanism requiring the user to give two or more verification factors to access a resource such as an application, an online account, or a VPN, which decreases the possibility of a cyber-attack. MFA is essential to an effective identity and access management (IAM) policy.
Why Is MFA Important?
MFA is essential because of the following reasons:
Protect Against Weak Employee Passwords
People are lousy at setting strong passwords, despite repeated reminders of the significance of password security. In reality, according to a recent NordPass survey, """"123456,"""" """"password,"""" and """"qwerty"""" are still among the most regularly used passwords worldwide. Similarly, a Ponemon Institute survey released earlier this year discovered that 50% of IT employees repeat passwords across several business accounts. Lastly, according to Verizon's 2020 Data Breach Investigations Report, 80 percent of hacking-related breaches utilized passwords in some form, either through stolen credentials or brute force assaults.
By forcing users to submit numerous credentials before accessing accounts, hackers are prohibited from entering your network using stolen passwords, devices, or other pieces of information. According to a recent Ping Identity poll, security and IT experts believe that multi factor authentication is the most effective security measure for securing on-premises and public cloud data.
Allow Your Other Security Measures To Function Properly
Although anti-virus software and powerful firewalls are good at securing corporate systems, they keep an access tunnel available for employees to connect to the network. If an attacker uses stolen credentials to obtain access, they can circumvent any other security measures, rendering them obsolete. MFA stops malicious actors from getting network access using a stolen password, allowing other security technologies to function properly. Furthermore, MFA may serve as a warning system, alerting you to unwanted access attempts. Workers only need to report instances when they are requested for secondary authentication that they did not request.
Supported By Single Sign On (SSO)
MFA may be integrated with a single sign on authentication and incorporated into apps. Thus, Multi Factor Authentication work types allows users to no longer have to generate several unique passwords or take the dangerous step of reusing the same password for different apps. Furthermore, in conjunction with SSO, MFA eliminates friction while authenticating the user's identity, saving time and increasing productivity.
How Does Multi Factor Authentication Work?
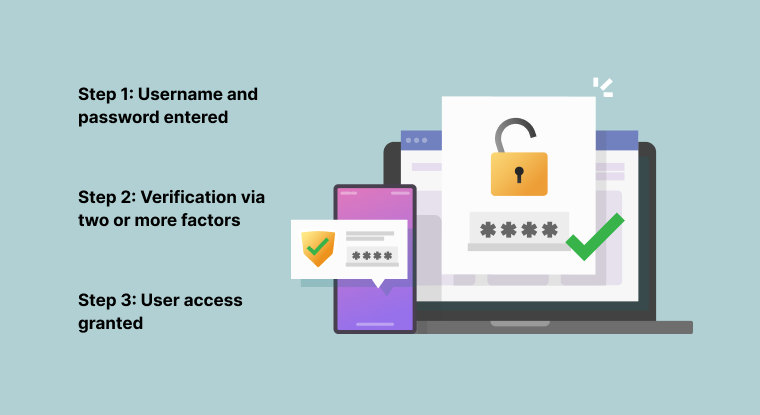
When an end-user connects to an account, they may provide their username and password as usual. They are then prompted to authenticate their identity with a few alternatives. This can involve receiving a one-time password (OTP) by SMS or an authenticator app or using an authentication software to enter biometric information such as a fingerprint or facial scan. Some corporate companies may prefer that users authenticate via a physical token, such as a key or swipe card. Many workplace MFA SSO authorization solutions also provide adaptive authentication, a sort of user authentication aimed at making it simpler for users to get access to essential systems while maintaining account security.
Multi Factor Authentication Work Types?
Authentication Using SMS Token
This check, which is usually in the form of a text message including a PIN number, is a reasonably simple precaution to adopt, especially for customers and the general public. This PIN is then used as a one-time password (OTP) in conjunction with standard username-and-password verification.
If your consumers commonly use mobile devices to access your services, it's a good idea to provide them with this or another mobile device-based authentication mechanism to assist in streamlining the consumer journey.
Authentication Through Email Token
This approach is similar to SMS tokens. However, the code is delivered by email. Generally, not everyone always has their phone with them, so it's a good idea to have this alternative. If your customer's mobile device is misplaced, it can also serve as a backup.
Authentication Using Hardware Token
As long as the key stays in the consumer's hands, using a separate hardware token is considered one of the most secure authentication techniques available. This option is relatively expensive, but it might be cost-effective to supply free dongles to your high-value customers.
Business clients are more ready to go the extra mile to utilize a hardware token, and their use is expanding. To utilize it, users just put the hardware token into their device. They may require an additional dongle if they utilize a mobile device for access.
Authentication Using A Software Token
You may get almost the same degree of security as a hardware token by utilizing an authentication software on a mobile device. In essence, the smart gadget serves as a token. This may be integrated with services such as Google Authenticator. Getting clients to utilize a third-party solution may inspire them to adopt MFA for other services outside of your company, boosting their overall security. It is also a good substitute for carrying an extra dongle to connect a hardware token to a smart device.
Biometric Authentication
As part of MFA single sign on authorization, those with a smart device or computer with biometric authentication (such as fingerprint ID or face recognition) can use this check to validate their identity. Customers find it less unpleasant to utilize biometric ID verification more frequently than typing in an OTP. Because of the decreased friction, it is an excellent choice when additional inspections are unavoidable.
What Is The Difference Between Multi-Factor Authentication (MFA) And Two-Factor Authentication (2FA)?
2FA is an additional layer of security used to ensure that anyone attempting to access an online account is who they claim to be. A user first provides their username and password. Instead of immediate access, they are then required to supply further information. This might be a fingerprint or a personal identification number (PIN).
Despite the fact that both 2FA and MFA offer additional security measures beyond single login and password credentials, they each provide varying levels of assurance that the person accessing the account is real.
MFA is only as safe as the authentication techniques that are used. The layered approach improves security. However, the low intrinsic security of a few authentication methods may persist even with MFA. As an example, consider a password, one-time password (OTP), and FaceID authentication are more secure than only using a password, but both passwords and OTP methods are weak in security. A 2FA is utilized by an account that supports Recognition Signals, such as location behavior and Mobile Push, both of which are difficult to break. As a result, every MFA approach is only as effective as the tactics employed.
Furthermore, the more levels of protection added to MFA, the better it becomes. This provides an additional layer of security than a 2FA system, which involves only two levels of protection.
Summing It Up
MFA single sign on configuration is often affordable and simple to use. It offers straightforward but efficient protection to individual users as well as the larger enterprise network. It is not only the finest way to safeguard your login procedure, but it also tells your consumers that you care about and take their security seriously. All in all, multifactor authentication allows you to strike a balance between consumer experience and today's security standards.
One of the best multi factor authentication single sign-on solution available on the market is NinjaAuth by 500apps. This platform allows two-factor authentication that enables users to connect to websites and applications using their mobile devices. Thus, it increases the security of the login procedure and protects user accounts against illegal access.
There are plenty of other features offered by NinjaAuth, which are bound to make your applications more secure. Visit the 500apps website to learn more.
Know Why NinjaAuth is the Best for Single Sign-On Solution?
Join the SaaS Revolution
-
All-in-One Suite of 50 apps
-
Unbelievable pricing - â¹999/user
-
24/5 Chat, Phone and Email Support
Infinity Suite
Tags
Email Finder Author Finder Email Validator Email List Email Hunter Email Checker Email Lookup Email Extractor Email Address Finder Email Scraper Find Emails CRM Software CRM Sales CRM CRM Software Enterprise CRM Software Cloud CRM Software Sales Enablement Workflow Automation Retail CRM Call Center CRM Real Estate CRM Sales Tool SDR Software Sales Engagement Platform Sales Qualified Leads Lead Management Tool Sales Tracking Sales Automation Outbound Sales Sales Prospecting Follow Up Leads Lead Management Call Center Software Call Center Software Outbound Call Center Auto Dialer Software Dialer Call Monitoring Automatic Call Distributor Answering Machine Detection Cloud Contact Center Software Virtual Call Center Call Management Time Tracking Time Tracking Employee Monitoring Time Tracker Time Tracking Software Timesheet Employee Time Clock Employee Tracking App Timekeeping Tracking App Time Clock App Applicant Tracking System ATS Applicant Tracking System Application Tracking System Applicant Software Recruiting Software ATS System Applicant Tracking Applicant Tracker Recruitment Software Candidate Relationship Management Systems Video Interviews Assessment Management Recruitment Software Video Interview Virtual Interview Coding Interview Interview Tool Online Assessment Employment Assessment Test Position Management Hiring App HRMS Software Human Resource Management HRMS Software HR Software Payroll Software Human Resource Software Employee Onboarding HRMS HR System Employee Management Document Management AI Writer Lead Enrichment AI Email Writer Sales Pitch Writer AI LinkedIn Outreach SEO Email writer Backlink Email Writer LinkedIn Chrome Extension Opening Line Writer Lead Generation Linkedin Search Prospect Lead Generation Sales Generation Data Enrichment CRM Integrations Technology Search Search with Email Integrations Website Search OKR Tool KPI OKR Task Management Performance Review Employee Performance Evaluation Employee Review Performance Management System OKR Goals MBO Email Notifications Learning Management System LMS Elearning Enterprise Learning Management Professional Development Employee Training Learning Management System Learning Platform Asynchronous Learning Training Management Knowledge Management Chatbot Chatbot AI Chatbot Customer Service Chatbot Online Chatbot Create Chatbot Messenger Chatbot Chatbot Software Website Chatbot Software Survey Bot Bot Builder Help Desk Software Ticketing Tool User Experience Help Desk Software Ticketing System Helpdesk Ticketing System Feedback Management Service Desk Software Support Ticketing Software Helpdesk Support Software Customer Service Ticketing System Live Chat Customer Service Software Live Chat Software Live Chat App Live Chat System Website Live Chat Live Chat Tool Web Chat Software Live Chat Support Software Customer Service Tool Live Chat Service Customer Feedback Customer Feedback Survey Customer Feedback Management Software Feedback Management Tool Customer Satisfaction Survey Software Customer Feedback Management System Client Feedback Software Survey Analysis Feedback Survey Software Feedback Management System User Feedback Software Customer Onboarding Customer Success Management Onboarding Process Workflows Customer Retention Customer Journey Onboarding Checklist User Segmentation Personalization Customized Templates Popup Builder API Platform End To End API Management Unified API Control REST API Management Web API Gateway API Documentation API Management API Integration API Development Unlimited Projects API Gateway Single Sign on Authentication Software Application Management Password Management SSO Configuration SSO Single Sign-On Access Management Easy Set-Up Single Login Secure Login App Builder App Builder Platform Low Code Application Platforms Low Code Development Build Your Own App Low Code App Software Drag And Drop Builder Custom Application Low Code Platform Low Code No Code Bespoke Software App Widgets Custom Widget File Picker Playground OAuth Keys File Manager Website Monitoring Reporting Web Application Monitoring Website Monitoring App Monitoring Performance Monitor App Baseline Analysis Location Insights Alerting System Reporting Wireframe Tool Design UI UX Project Management Mock Designer Wireframe Designer Website Mockup UI Prototyping Image Library Project Management Real-Time Updates Design UI UX Website Builder Website Builder Webpage Builder Website Creator Landing Page Creator Website Maker Blog Builder Ecommerce Website Builder Website Analytics Website Development Landing Page Builder Email Marketing Email Marketing Software Bulk Email Sender Automated Email Email Campaign Systems Email Automation Software Autoresponders Email Blast Service Email Marketing Email Marketing Automation Drip Campaigns Social Media Management Instagram Post Scheduler Social Media Analytics Social Media Management Social Media Planner Social Media Calendar Social Media Scheduling Social Media Listening Social Media Monitoring Social Listening SEO Tool Keyword Tool Link Building SEO Optimizer Website Audit On-Page SEO Broken Link Checker Rank Tracker Website Grader SEO Competitor Analysis Website Recording Website Analytics Click Tracking Usability Testing Website Monitoring Mouse Tracking Visitor Recording Session Replay Conversion Funnels Website Recording Website Visitor Tracker Website Personalization Lead Generation Tool Popup Maker Lead Generation Software Popup Builder Website Personalization Software Lead Capture Software Popup Builder Lead Capture Tool Lead Generation App Website Personalization App Content Planner Content Planner AI Writer Social Media Content Planner Ai Content Writer Social Media Content Calendar Content Generator AI Blog Writer Content Marketing Software Social Media Calendar Social Media Planner Push Notification Push Notification Push Messages Push Notification Service Push Service Push Notification App Custom Notifications Mobile Push Notifications Push Notification For Website Push Notification Tool Push Notification Providers Image Personalization Email Marketing Template Countdown Clock Personalization Software Personalized Software Countdown Clock Countdown Timer In Email Personalization Tool Personalized Images Personalized Videos Conversational Chatbot PPC Management Keyword Research PPC Management PPC Marketing Keyword Finder Keyword Generator Shopping Ads Adwords Reports Keyword Research Tool Keyword Suggestion Tool Team Chat Team Chat Software Collaboration Software Team Collaboration Team Communication Online Collaboration Collaboration Tool Teamwork Collaboration Virtual Communication Team Collaboration Software Business Phone System Virtual Phone Numbers Virtual PBX Toll Free Numbers Business Phone System IVR PBX Small Business Phone System PBX System VoIP Phone Cloud Phone Video Conferencing Video Conferencing Video Call Recording Virtual Conferencing Software Virtual Meetings Virtual Meeting Platforms Virtual Conference Platforms Online Conference Platforms Video Calling Software Cloud Meetings Video Conferencing Software Email Provider Email Software Software For Emails Hosted Emails Email With Domain Custom Email Address Email Hosting Business Email Address Email Encrypted Custom Domain Email Project Management Software Project Management Task Management Project Planner Project Management Tool Task Management Software Project Planning Software Project Management App Task Management App Project Management System Project Management Software Form Builder Form Builder Survey Builder Order Forms Web Forms Form Maker Form Creator Form Designer Survey Maker Survey Creator Custom Form Appointment Scheduling Appointment Scheduling Software Appointment Scheduling System Meetings Scheduler Appointment Scheduling App Online Appointment Scheduling Online Scheduling App Appointment Scheduler Appointment Booking App Calendar Scheduler Online Scheduler Robotic Process Automation RPA Tools RPA RPA Automation Robotic Automation Software Data Scraper Web Scraper Robotic Automation Website Scraper Business Process Automation Robotic Process Automation Business Process Management Workflow Management Business Process Modelling Business Process Automation BPMN BPM Software BPM Tool Business Process Management Workflow Software Workflow Automation Business Process Mapping App Integration Workflow Software Workflow App Workflow Automation Process Automation Application Integration Data Integration Tool Workflow Management Software Data Integration Software Workflow Tool Marketing Automation Electronic Signature Signature Maker Digital Signature Software Digital Signature Pdf Signer Esign Online Signature Signature Creator Sign Documents Online Electronic Sign E Signature
