What Is User Authentication Software? Learn in Detail
A user authentication software ensures that users have proper authentication to access an application or service. The software helps businesses easily verify the user identity and provides them with credentials only with the proof of their authenticity. Let’s dive in to understand better.

The human-to-computer network interactions can either allow or prevent cyberattacks. Business organizations adopt multiple measures to secure web applications and grant access to authorized users. It is where user authentication software comes into the picture.
User authentication software prevents unauthorized users from accessing networks or devices. The process identifies users who request access to a network, system, device, or resources. The best part about user authentication software is that it prevents hackers or attackers from accessing sensitive information. It is a login procedure where users get requested personalized passwords to get authorized access to multiple systems. The Authentication fails if a user does not have proper login rights into the system.
So, user authentication software covers all human-to-computer interactions that require user registration and login attempts. The process verifies user responses and decides who can access the system. You will find multiple authentication methods like a single sign on service, multifactor authentication, identity access management, etc. We will discuss the authentication methods in detail below.
Importance of User Authentication software

User authentication software enables organizations to keep their networks secure and permits authenticated users or processes to access protected resources like computer systems, databases, networks, websites, and other applications and services. The process ensures information privacy and financial safety and helps prevent private security threats, hacks, fraud, and cyberattacks.
The following sections will help you learn about the importance of user authentication software.
Confidentiality and Privacy
User authentication software helps business organizations protect their customer’s identity, confidentiality, and privacy of information by using unique passwords and usernames. The process proves helpful for transactions and systems that happen online where a user has to provide the username and the password. If the user is unable to log in, the activity fails.
So, user authentication software ensures that only genuine users can access systems by proving their identities. The process enables easy management of user identities in organizational systems.
Theft Prevention
User authentication software includes an access control system that restricts access to unauthorized users. The process is critical when an attacker gets sufficient access to an individual’s account information to alter or steal the owner’s identity. Multiple websites require the personal information of customers to provide services. So, the websites must have an access control system to keep the information secure. User authentication software helps businesses keep information secure via the easy setup of such control systems.
Varying Security Levels
Control systems have evolved with technology and time. So, passwords and PINs are not the only options available for individuals who want to keep their information secure. User authentication software is available in multiple tools and systems like identity management software and password management software. Such authentication software offers varying security levels to businesses and their clients and customers to help keep their information safe and secure.
Various Forms of Authentication
Authentication is the best and foremost line of defense for cybersecurity. The process determines whether the users are who they say they are. Authentication is the best way to confirm digital identification which requires users to have different permission levels to access or perform tasks on various organizational systems and resources.
You will find multiple authentication technologies, from fingerprints to passwords, to confirm user identity and allow access to user access management tasks. The process provides protection and prevents security and data breaches.
We will discuss the various authentication forms below.
Single-factor Authentication
A single factor is the most common authentication form and requires one factor to access systems. The verification factor can be a password, username, code, or pin number. Single-factor authentication systems are user-friendly and flexible to use for business organizations.
However, single-factor Authentication is the least secure authentication system because it requires one factor to access a complete system. So, the system gets prone to attacks like phishing, mere guessing, and keylogging.
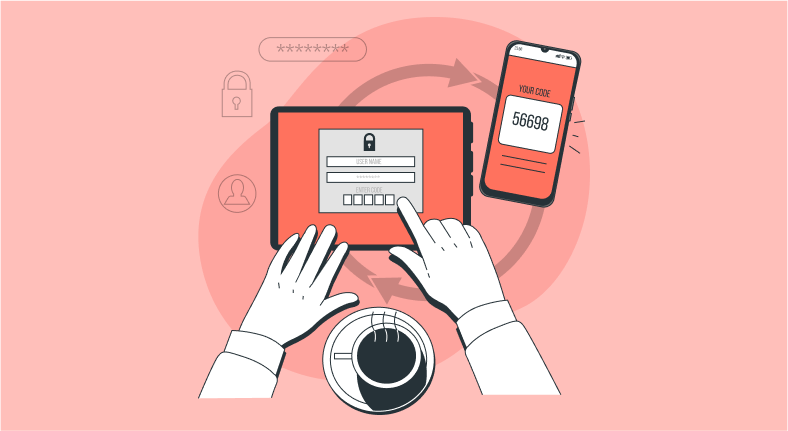
Two-factor Authentication
The two-factor authentication system reinforces security efforts by adding a second verification factor to the primary one. The added factor double-checks that the user is who they are and foils attempts by hackers to attack a system. Users must enter their primary authentication credentials in the system and then input secondary identifying information for validation.
The secondary verification is tough because it requires the user to provide something that is not easily accessible and is unrelated to the system. Secondary factors include one-time passwords from authenticator apps, a phone number, or a device that will receive a push notification or SMS code, voice recognition, fingerprint, or face ID.
Two-factor Authentication minimizes system risks or resource compromises because it is unlikely that an invalid user would have access to both authentication factors.
Single Sign-On Solution
Users can log in to a single application and gain access to multiple applications by doing so using a sso Single Sign On Solution. The top sso providers are a convenient way for users because they do not have to remember multiple sets of credentials, and it creates a seamless experience for operative sessions.
Organizations identify a central domain and create a secure single sign on system that link resources. The process enables domain-monitored user authentication software and ensures that only valid users can end their sessions and successfully log out of the applications and linked resources.
Multifactor Authentication
Multifactor Authentication is one of the most high-assurance security methods because it uses system-relevant factors to legitimize users. The security technology uses biometrics, additional passwords, device-based confirmations, locations, or behavior-based information to confirm user identities before providing access to systems.
The best part about multi factor authentication software is that it provides multiple security measures for organizations to keep their systems safe.
Summing It Up
User authentication software verifies user identities to gain network access or a computing resource by authorizing credentials during interactions to ensure system security. Authentication is the best security process that prevents unauthorized access to systems and allows only valid users to log in and out of linked resources.
NinjaAuth by 500apps is a reliable single sign-on solution software that helps set up organizational Authentication to keep the system safe. The best part about the software is that it ensures data security and helps boost team productivity within organizations. The software also offers a centralized access management system for all applications under a single platform. So, if your organization is looking for the best single sign-on solutions, NinjaAuth is your answer.
Know Why NinjaAuth is the Best for Single Sign-On Solution?
Join the SaaS Revolution
-
All-in-One Suite of 50 apps
-
Unbelievable pricing - â¹999/user
-
24/5 Chat, Phone and Email Support
Infinity Suite
Tags
Email Finder Author Finder Email Validator Email List Email Hunter Email Checker Email Lookup Email Extractor Email Address Finder Email Scraper Find Emails CRM Software CRM Sales CRM CRM Software Enterprise CRM Software Cloud CRM Software Sales Enablement Workflow Automation Retail CRM Call Center CRM Real Estate CRM Sales Tool SDR Software Sales Engagement Platform Sales Qualified Leads Lead Management Tool Sales Tracking Sales Automation Outbound Sales Sales Prospecting Follow Up Leads Lead Management Call Center Software Call Center Software Outbound Call Center Auto Dialer Software Dialer Call Monitoring Automatic Call Distributor Answering Machine Detection Cloud Contact Center Software Virtual Call Center Call Management Time Tracking Time Tracking Employee Monitoring Time Tracker Time Tracking Software Timesheet Employee Time Clock Employee Tracking App Timekeeping Tracking App Time Clock App Applicant Tracking System ATS Applicant Tracking System Application Tracking System Applicant Software Recruiting Software ATS System Applicant Tracking Applicant Tracker Recruitment Software Candidate Relationship Management Systems Video Interviews Assessment Management Recruitment Software Video Interview Virtual Interview Coding Interview Interview Tool Online Assessment Employment Assessment Test Position Management Hiring App HRMS Software Human Resource Management HRMS Software HR Software Payroll Software Human Resource Software Employee Onboarding HRMS HR System Employee Management Document Management AI Writer Lead Enrichment AI Email Writer Sales Pitch Writer AI LinkedIn Outreach SEO Email writer Backlink Email Writer LinkedIn Chrome Extension Opening Line Writer Lead Generation Linkedin Search Prospect Lead Generation Sales Generation Data Enrichment CRM Integrations Technology Search Search with Email Integrations Website Search OKR Tool KPI OKR Task Management Performance Review Employee Performance Evaluation Employee Review Performance Management System OKR Goals MBO Email Notifications Learning Management System LMS Elearning Enterprise Learning Management Professional Development Employee Training Learning Management System Learning Platform Asynchronous Learning Training Management Knowledge Management Chatbot Chatbot AI Chatbot Customer Service Chatbot Online Chatbot Create Chatbot Messenger Chatbot Chatbot Software Website Chatbot Software Survey Bot Bot Builder Help Desk Software Ticketing Tool User Experience Help Desk Software Ticketing System Helpdesk Ticketing System Feedback Management Service Desk Software Support Ticketing Software Helpdesk Support Software Customer Service Ticketing System Live Chat Customer Service Software Live Chat Software Live Chat App Live Chat System Website Live Chat Live Chat Tool Web Chat Software Live Chat Support Software Customer Service Tool Live Chat Service Customer Feedback Customer Feedback Survey Customer Feedback Management Software Feedback Management Tool Customer Satisfaction Survey Software Customer Feedback Management System Client Feedback Software Survey Analysis Feedback Survey Software Feedback Management System User Feedback Software Customer Onboarding Customer Success Management Onboarding Process Workflows Customer Retention Customer Journey Onboarding Checklist User Segmentation Personalization Customized Templates Popup Builder API Platform End To End API Management Unified API Control REST API Management Web API Gateway API Documentation API Management API Integration API Development Unlimited Projects API Gateway Single Sign on Authentication Software Application Management Password Management SSO Configuration SSO Single Sign-On Access Management Easy Set-Up Single Login Secure Login App Builder App Builder Platform Low Code Application Platforms Low Code Development Build Your Own App Low Code App Software Drag And Drop Builder Custom Application Low Code Platform Low Code No Code Bespoke Software App Widgets Custom Widget File Picker Playground OAuth Keys File Manager Website Monitoring Reporting Web Application Monitoring Website Monitoring App Monitoring Performance Monitor App Baseline Analysis Location Insights Alerting System Reporting Wireframe Tool Design UI UX Project Management Mock Designer Wireframe Designer Website Mockup UI Prototyping Image Library Project Management Real-Time Updates Design UI UX Website Builder Website Builder Webpage Builder Website Creator Landing Page Creator Website Maker Blog Builder Ecommerce Website Builder Website Analytics Website Development Landing Page Builder Email Marketing Email Marketing Software Bulk Email Sender Automated Email Email Campaign Systems Email Automation Software Autoresponders Email Blast Service Email Marketing Email Marketing Automation Drip Campaigns Social Media Management Instagram Post Scheduler Social Media Analytics Social Media Management Social Media Planner Social Media Calendar Social Media Scheduling Social Media Listening Social Media Monitoring Social Listening SEO Tool Keyword Tool Link Building SEO Optimizer Website Audit On-Page SEO Broken Link Checker Rank Tracker Website Grader SEO Competitor Analysis Website Recording Website Analytics Click Tracking Usability Testing Website Monitoring Mouse Tracking Visitor Recording Session Replay Conversion Funnels Website Recording Website Visitor Tracker Website Personalization Lead Generation Tool Popup Maker Lead Generation Software Popup Builder Website Personalization Software Lead Capture Software Popup Builder Lead Capture Tool Lead Generation App Website Personalization App Content Planner Content Planner AI Writer Social Media Content Planner Ai Content Writer Social Media Content Calendar Content Generator AI Blog Writer Content Marketing Software Social Media Calendar Social Media Planner Push Notification Push Notification Push Messages Push Notification Service Push Service Push Notification App Custom Notifications Mobile Push Notifications Push Notification For Website Push Notification Tool Push Notification Providers Image Personalization Email Marketing Template Countdown Clock Personalization Software Personalized Software Countdown Clock Countdown Timer In Email Personalization Tool Personalized Images Personalized Videos Conversational Chatbot PPC Management Keyword Research PPC Management PPC Marketing Keyword Finder Keyword Generator Shopping Ads Adwords Reports Keyword Research Tool Keyword Suggestion Tool Team Chat Team Chat Software Collaboration Software Team Collaboration Team Communication Online Collaboration Collaboration Tool Teamwork Collaboration Virtual Communication Team Collaboration Software Business Phone System Virtual Phone Numbers Virtual PBX Toll Free Numbers Business Phone System IVR PBX Small Business Phone System PBX System VoIP Phone Cloud Phone Video Conferencing Video Conferencing Video Call Recording Virtual Conferencing Software Virtual Meetings Virtual Meeting Platforms Virtual Conference Platforms Online Conference Platforms Video Calling Software Cloud Meetings Video Conferencing Software Email Provider Email Software Software For Emails Hosted Emails Email With Domain Custom Email Address Email Hosting Business Email Address Email Encrypted Custom Domain Email Project Management Software Project Management Task Management Project Planner Project Management Tool Task Management Software Project Planning Software Project Management App Task Management App Project Management System Project Management Software Form Builder Form Builder Survey Builder Order Forms Web Forms Form Maker Form Creator Form Designer Survey Maker Survey Creator Custom Form Appointment Scheduling Appointment Scheduling Software Appointment Scheduling System Meetings Scheduler Appointment Scheduling App Online Appointment Scheduling Online Scheduling App Appointment Scheduler Appointment Booking App Calendar Scheduler Online Scheduler Robotic Process Automation RPA Tools RPA RPA Automation Robotic Automation Software Data Scraper Web Scraper Robotic Automation Website Scraper Business Process Automation Robotic Process Automation Business Process Management Workflow Management Business Process Modelling Business Process Automation BPMN BPM Software BPM Tool Business Process Management Workflow Software Workflow Automation Business Process Mapping App Integration Workflow Software Workflow App Workflow Automation Process Automation Application Integration Data Integration Tool Workflow Management Software Data Integration Software Workflow Tool Marketing Automation Electronic Signature Signature Maker Digital Signature Software Digital Signature Pdf Signer Esign Online Signature Signature Creator Sign Documents Online Electronic Sign E Signature
