How to Choose the Best Identity Management Software Solution
Read this article to know how to choose the best identity management software solution for your business. Allow you to achieve your identity management goals.

Stealing passwords and hacking into networks have become easier than ever with improvements in current technology, emphasizing the significance of identity and access management. More significantly, if your data is not entirely secret, a breach anywhere on the system might jeopardize everyone's data. This is why it is critical to take advantage of the security benefits of identity access management.
What Is Best Identity Management Software Solution?
Identity management software, which is also referred to as identity and access management (IAM), guarantees that only authorized individuals have access to the technological resources required to execute their job tasks. It encompasses policies and technology that cover an organization-wide process for correctly identifying, authenticating, and authorizing individuals, groups of individuals, or software applications using qualities such as user access rights and constraints based on their identities. Identity management systems secure not just software and data access but also an enterprise's physical resources, such as servers, networks, and storage devices, against illegal access, which might lead to a ransomware assault. Identity management software has grown in relevance over the last decade as a result of an increasing number of worldwide regulatory, compliance, and government regulations aimed at protecting sensitive data from any form of exposure.
The Benefits Of a best Identity Management Software Solution
Simplifies Reporting And Auditing
Single sign-on (SSO) makes it easy for IT teams to examine where and how user credentials are used by consolidating user identities and passwords. When user credentials are hacked, IAM systems assist IT departments in determining which user was affected and whose data was accessed during the attack. Furthermore, systems with detailed audit trails can record user provisioning and de-provisioning as employees are on-boarded or terminated.
Administration Time Saved
Administrative expenses can quickly add up. An efficient and simple solution for allowing users to readily access their workspace and databases will save time if additional challenges arise. IAM now enables a continuous continuation of work. A corporation can alter access settings, create privileged groups, and simplify user registration processes with an easy management flexible administration. In addition, a company can start building application procedures, user approval, and access modification based on its needs. When things are fully deployed, they are set and ready to go, promoting workplace efficiency.
Enhanced Security
Identity access management benefits also improve security by carefully controlling access controls to user accounts and apps. Adapting access to the user's digital identity with flexibility enables administrators to monitor operations and, in the case of security problems, identify their source. It is essential to remember that the search for identity access management solutions is strategic for customers as well as contributes to the safety of personal and corporate data in the company network.
Monitoring Access Is Possible
Identity Management software must guarantee that digital identity controls and access are carried out in order to balance the assessments that administrators must perform by automating procedures and preserving decision agility. One of the essentialt methods to achieve this agility and automation without sacrificing the capacity to access controls is to correlate their jobs with organizational positions and hierarchies. We may also utilize the business units, the geographies in which they are situated, and other factors to determine the importance of access to certain information.
Excellent Information Sharing
Information is frequently lost or confused among huge gatherings of individuals. Data may be difficult to access, and file sharing may be problematic. There is a lot of room for sharing with IAM. As these good frameworks provide a single shared platform, information sharing is straightforward. Furthermore, it is simple to search and exchange files, knowing that you are engaging with your colleagues or clients securely and respectably. This provides value to the organization by instilling trust. As a result, deciding to transition to IAM is a critical step for every corporation.
How To Choose The Best Identity Management Software?
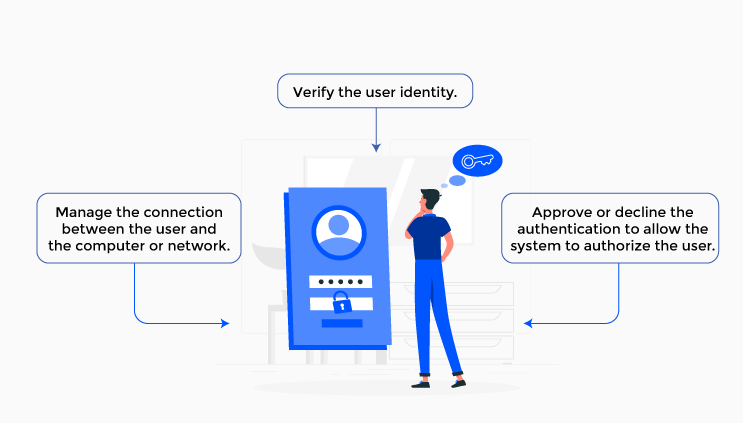
It might be difficult to select the best access management software. As a result, we developed four brief pointers on what things to look for during this process.
First And Foremost, Compatibility Is Essential
You must find a system that can adapt to several types of directories, such as Microsoft Active Directory. You must ensure that your databases, application servers, and business-critical applications are supported. Based on the materials available, you must also determine if interoperability with on-premises and cloud apps is equally supported.
Look For A Tool That Makes The Entire Process Easier
Nothing is more crucial than usability. It is critical to have a smooth connection that allows for simple addition, modification, deletion, support for all login policies, and the ability to write multiple identity stores.
Determine How Much Leeway To Provide Users
Internally defining user access is a critical step toward proper identity management. You and your IT and security teams must decide if you want your end-users to be able to change passwords or update their profiles without the requirement for administrator participation. Find a program that allows you to configure these rights in accordance with your company's policies.
Your Tool Must Evolve Alongside You
Everyone speaks about whether or not company strategies are scalable. The same may be said for your identity management systems. As your user base expands, your solution should be able to meet that demand without sacrificing quality. It's as simple as that.
Here are some features you must look for when choosing Identity Management Software.
One-Time Password
Everything in your infrastructure must be integrated into the same single sign-on solution. Thus, you only need to sign in once to access everything. This not only improves the user experience but also promotes security. Users do not need to manage numerous authentication providers, and IT is not required to manage various permissions.
By connecting all of your systems, you also ensure that your IT team will detect problems in the authentication system much more quickly. IT just needs to maintain the security of a single system and a single login user account for each employee.
Management Of Privileged Accounts
Many businesses establish more privileged accounts for employees at higher levels of the firm, even when it isn't absolutely necessary. Privileged accounts can expose a system to significant risk. Thus, the system should handle privileged accounts and should notify the IT department if privileged accounts are used inappropriately. Privileged accounts should not be utilized for day-to-day work; instead, they should only be used for the purposes for which they were created.
Services For Automatic Provisioning
The more that can be done automatically, the less likely errors are to occur, and the more time IT can devote to other, more critical activities. Automatic provisioning services lower the amount of labor required by an IT staff while also delivering enhanced, automated procedures that can subsequently be standardized.
Access Control Based On Roles
Today, a good infrastructure is a zero-trust infrastructure. Role-based access control can help with this by assigning users particular responsibilities and limiting permissions to only what is required. Role-based access controls can also significantly decrease possible compromise risks. Lastly, companies can better regulate their rights automatically using role-based access control.
Summing It Up
As we are using more data in business, a powerful and secure system is required. Securing all platforms and devices will provide you with peace of mind and the assurance of a solid business, while users and customers will be satisfied with their workload and will be relieved of the responsibilities of technology becoming slow, obsolete, or difficult to run.
The delivery of IAM as software enables any firm to better manage its application. In fact, with IAM, a company's operations, management, and implementation can be considerably improved. Users may collaborate harmoniously on a platform that operates and combines all the latest technologies in one location with great security.
A solution like NinjaAuth by 500apps offers a single login point for all applications, which you can use to boost user efficiency. This also eliminates the need to remember several usernames and passwords. Furthermore, NinjaAuth is easy to set up. All you need to do is simply copy and paste the supplied code into your website or application.
All in all, NinjaAuth simplifies all areas and is an ideal business choice for 2022 and beyond.
Know Why NinjaAuth is the Best for Single Sign-On Solution?
Join the SaaS Revolution
-
All-in-One Suite of 50 apps
-
Unbelievable pricing - â¹999/user
-
24/5 Chat, Phone and Email Support
Infinity Suite
Tags
Email Finder Author Finder Email Validator Email List Email Hunter Email Checker Email Lookup Email Extractor Email Address Finder Email Scraper Find Emails CRM Software CRM Sales CRM CRM Software Enterprise CRM Software Cloud CRM Software Sales Enablement Workflow Automation Retail CRM Call Center CRM Real Estate CRM Sales Tool SDR Software Sales Engagement Platform Sales Qualified Leads Lead Management Tool Sales Tracking Sales Automation Outbound Sales Sales Prospecting Follow Up Leads Lead Management Call Center Software Call Center Software Outbound Call Center Auto Dialer Software Dialer Call Monitoring Automatic Call Distributor Answering Machine Detection Cloud Contact Center Software Virtual Call Center Call Management Time Tracking Time Tracking Employee Monitoring Time Tracker Time Tracking Software Timesheet Employee Time Clock Employee Tracking App Timekeeping Tracking App Time Clock App Applicant Tracking System ATS Applicant Tracking System Application Tracking System Applicant Software Recruiting Software ATS System Applicant Tracking Applicant Tracker Recruitment Software Candidate Relationship Management Systems Video Interviews Assessment Management Recruitment Software Video Interview Virtual Interview Coding Interview Interview Tool Online Assessment Employment Assessment Test Position Management Hiring App HRMS Software Human Resource Management HRMS Software HR Software Payroll Software Human Resource Software Employee Onboarding HRMS HR System Employee Management Document Management AI Writer Lead Enrichment AI Email Writer Sales Pitch Writer AI LinkedIn Outreach SEO Email writer Backlink Email Writer LinkedIn Chrome Extension Opening Line Writer Lead Generation Linkedin Search Prospect Lead Generation Sales Generation Data Enrichment CRM Integrations Technology Search Search with Email Integrations Website Search OKR Tool KPI OKR Task Management Performance Review Employee Performance Evaluation Employee Review Performance Management System OKR Goals MBO Email Notifications Learning Management System LMS Elearning Enterprise Learning Management Professional Development Employee Training Learning Management System Learning Platform Asynchronous Learning Training Management Knowledge Management Chatbot Chatbot AI Chatbot Customer Service Chatbot Online Chatbot Create Chatbot Messenger Chatbot Chatbot Software Website Chatbot Software Survey Bot Bot Builder Help Desk Software Ticketing Tool User Experience Help Desk Software Ticketing System Helpdesk Ticketing System Feedback Management Service Desk Software Support Ticketing Software Helpdesk Support Software Customer Service Ticketing System Live Chat Customer Service Software Live Chat Software Live Chat App Live Chat System Website Live Chat Live Chat Tool Web Chat Software Live Chat Support Software Customer Service Tool Live Chat Service Customer Feedback Customer Feedback Survey Customer Feedback Management Software Feedback Management Tool Customer Satisfaction Survey Software Customer Feedback Management System Client Feedback Software Survey Analysis Feedback Survey Software Feedback Management System User Feedback Software Customer Onboarding Customer Success Management Onboarding Process Workflows Customer Retention Customer Journey Onboarding Checklist User Segmentation Personalization Customized Templates Popup Builder API Platform End To End API Management Unified API Control REST API Management Web API Gateway API Documentation API Management API Integration API Development Unlimited Projects API Gateway Single Sign on Authentication Software Application Management Password Management SSO Configuration SSO Single Sign-On Access Management Easy Set-Up Single Login Secure Login App Builder App Builder Platform Low Code Application Platforms Low Code Development Build Your Own App Low Code App Software Drag And Drop Builder Custom Application Low Code Platform Low Code No Code Bespoke Software App Widgets Custom Widget File Picker Playground OAuth Keys File Manager Website Monitoring Reporting Web Application Monitoring Website Monitoring App Monitoring Performance Monitor App Baseline Analysis Location Insights Alerting System Reporting Wireframe Tool Design UI UX Project Management Mock Designer Wireframe Designer Website Mockup UI Prototyping Image Library Project Management Real-Time Updates Design UI UX Website Builder Website Builder Webpage Builder Website Creator Landing Page Creator Website Maker Blog Builder Ecommerce Website Builder Website Analytics Website Development Landing Page Builder Email Marketing Email Marketing Software Bulk Email Sender Automated Email Email Campaign Systems Email Automation Software Autoresponders Email Blast Service Email Marketing Email Marketing Automation Drip Campaigns Social Media Management Instagram Post Scheduler Social Media Analytics Social Media Management Social Media Planner Social Media Calendar Social Media Scheduling Social Media Listening Social Media Monitoring Social Listening SEO Tool Keyword Tool Link Building SEO Optimizer Website Audit On-Page SEO Broken Link Checker Rank Tracker Website Grader SEO Competitor Analysis Website Recording Website Analytics Click Tracking Usability Testing Website Monitoring Mouse Tracking Visitor Recording Session Replay Conversion Funnels Website Recording Website Visitor Tracker Website Personalization Lead Generation Tool Popup Maker Lead Generation Software Popup Builder Website Personalization Software Lead Capture Software Popup Builder Lead Capture Tool Lead Generation App Website Personalization App Content Planner Content Planner AI Writer Social Media Content Planner Ai Content Writer Social Media Content Calendar Content Generator AI Blog Writer Content Marketing Software Social Media Calendar Social Media Planner Push Notification Push Notification Push Messages Push Notification Service Push Service Push Notification App Custom Notifications Mobile Push Notifications Push Notification For Website Push Notification Tool Push Notification Providers Image Personalization Email Marketing Template Countdown Clock Personalization Software Personalized Software Countdown Clock Countdown Timer In Email Personalization Tool Personalized Images Personalized Videos Conversational Chatbot PPC Management Keyword Research PPC Management PPC Marketing Keyword Finder Keyword Generator Shopping Ads Adwords Reports Keyword Research Tool Keyword Suggestion Tool Team Chat Team Chat Software Collaboration Software Team Collaboration Team Communication Online Collaboration Collaboration Tool Teamwork Collaboration Virtual Communication Team Collaboration Software Business Phone System Virtual Phone Numbers Virtual PBX Toll Free Numbers Business Phone System IVR PBX Small Business Phone System PBX System VoIP Phone Cloud Phone Video Conferencing Video Conferencing Video Call Recording Virtual Conferencing Software Virtual Meetings Virtual Meeting Platforms Virtual Conference Platforms Online Conference Platforms Video Calling Software Cloud Meetings Video Conferencing Software Email Provider Email Software Software For Emails Hosted Emails Email With Domain Custom Email Address Email Hosting Business Email Address Email Encrypted Custom Domain Email Project Management Software Project Management Task Management Project Planner Project Management Tool Task Management Software Project Planning Software Project Management App Task Management App Project Management System Project Management Software Form Builder Form Builder Survey Builder Order Forms Web Forms Form Maker Form Creator Form Designer Survey Maker Survey Creator Custom Form Appointment Scheduling Appointment Scheduling Software Appointment Scheduling System Meetings Scheduler Appointment Scheduling App Online Appointment Scheduling Online Scheduling App Appointment Scheduler Appointment Booking App Calendar Scheduler Online Scheduler Robotic Process Automation RPA Tools RPA RPA Automation Robotic Automation Software Data Scraper Web Scraper Robotic Automation Website Scraper Business Process Automation Robotic Process Automation Business Process Management Workflow Management Business Process Modelling Business Process Automation BPMN BPM Software BPM Tool Business Process Management Workflow Software Workflow Automation Business Process Mapping App Integration Workflow Software Workflow App Workflow Automation Process Automation Application Integration Data Integration Tool Workflow Management Software Data Integration Software Workflow Tool Marketing Automation Electronic Signature Signature Maker Digital Signature Software Digital Signature Pdf Signer Esign Online Signature Signature Creator Sign Documents Online Electronic Sign E Signature
