SSO Implementation Steps Best Practices
Users can access numerous company apps with a single set of login credentials thanks to Single Sign On (SSO), an authentication and authorisation technique with SSO Implementation Steps Best Practices
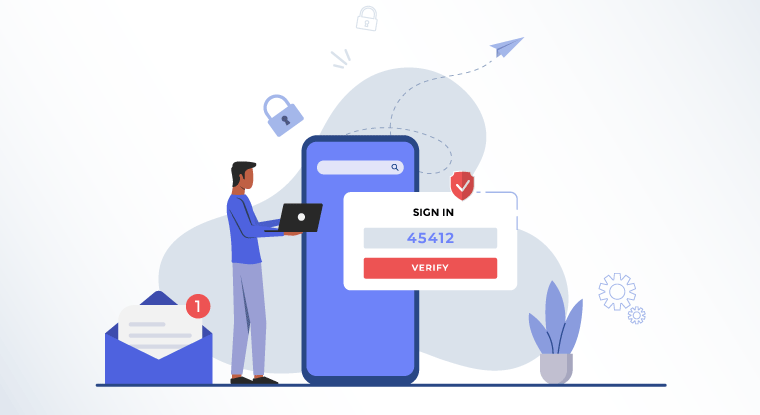
Single Sign On (SSO) is an authentication and authorization method that enables users to access various corporate applications using single login credentials. Simply said, SSO merges several application login windows into one, allowing you to enter credentials once and gain access to all apps without having to log in to each one individually. End-users save time and effort by not having to regularly sign in and out of a variety of online, on-premises, and cloud apps. SSO is a key component of identity access management (IAM) or access control services.
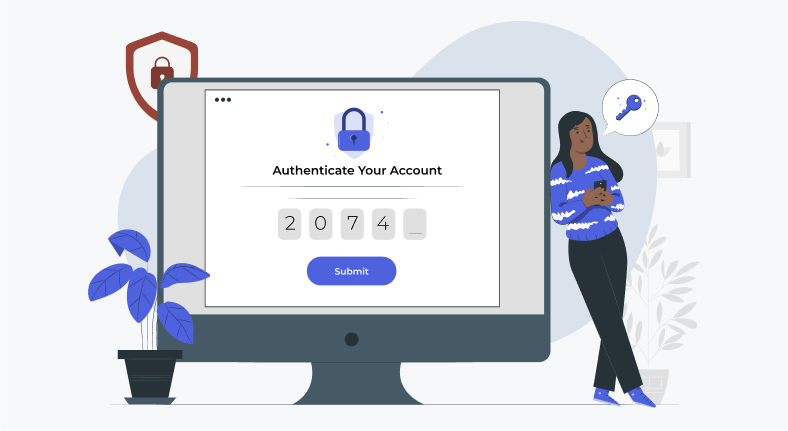
When an SSO solution is correctly deployed inside a business, it simplifies overall password management, enhancing productivity and security by reducing the chance of lost, weak, or forgotten passwords.`
Steps To Deliver An Effective SSO Architecture.
Single sign on solution like NinjaAuth by 500apps may require some steps to be completed to ensure an effective SSO architecture. Given below are those steps:
Review SSO Objectives As Part Of The Broader IAM Program
Investigate your alternatives for deploying SSO and choose the ones that make the most sense for your present and future organization. To keep ahead of the expanding demands on IAM infrastructure, businesses installing or reimplementing Single Sign On Solution should strive for IAM agility, which may allow them to respond to future changes in business objectives and security expectations.
Identify Users And Needs, Evaluate Capabilities, And Conduct A Gap Analysis
You must determine the organization's SSO needs, which may require many important decisions. Employees, business-to-business partners, and consumer SSO may have entirely different needs. Some businesses can find it challenging to implement an SSO solution for all sorts of users and all apps. Thus, in many cases, taking a staged approach and SSO Implementation Steps Best Practices a subset of user groups makes more sense.
Create An Architecture To Enable SSO
It is essential to consider whether the company has the expertise and resources to operate the SSO software safely and with high availability. You must choose whether to deploy SSO software on-premises, employ a cloud-based service such as IDaaS, an abbreviation for identity access management as a service, or implement a hybrid solution.
Determine Authentication Of User
One of the most important aspects of delivering SSO is ensuring that users are properly authenticated. It is essential to take an adaptive trust-based approach to user authentication in today's world of cyberattacks and phishing attempts. The continuous adaptive risk and trust assessment, also known as the CARTA technique, is a part of SSO that identifies corroboration and analyzes several signals, including affirmative signals that confirm the user is who they claim they are (such as device and IP address recognition) and negative signals that suggest elevated risk (such as aberrant behavior).
Evaluate Additional Requirements
After defining the overall architectural approach, you must consider various requirements particular to the enterprise, such as access to Microsoft Office 365, Amazon Web Services (AWS), and APIs. It is not always required for all employees to have SSO access to all the apps they use, especially if providing an SSO connection to a seldom-used application would be prohibitively expensive.
Using all these criteria, create a short list of the best Single Sign On Solution.
SSO Implementation Steps Best Practices
Here are a few of the best practices for single sign on that can help you utilize the tool more efficiently.
Password And Email Resets Are Not Permitted
You must utilize this feature and stop a user from changing or resetting his password over email. Companies typically prefer that a user only use her work email address since this is the email address that the firm owns. You must not allow the user only to convert it to a personal email address. This ensures data security and prevents your employees from accessing all company information by logging into a single platform. You can also limit your employees' access controls so that they do not view information that is not required to complete the current task.
Set Session Timeouts
Allow idle user sessions to expire rather than leaving a user signed in continuously. You may use the session timeout value from the SAML answer or have a per-account option. When a user hits a link in the app after the session has ended, your app should submit a SAML request to the identity provider to determine whether or not the user is still permitted to sign in to your app.
Sign-In Requirements
If the application receives a sign-on request but the user's browser already has an active session, replace it with a new session. This decreases the possibility of a user accidentally viewing someone else's data. Sign-in requirements, one of the best practices for single sign on, are also useful for users who utilize SSO portals to sign in to many accounts inside the same application.
Best Practices For Delegated Authentication
Delegated authentication is similar to single sign on, but it provides an alternate payment authentication method that does not compromise consumer experience or security. Issuers can delegate authentication to a third party. This might be an acquirer, a digital wallet provider, or you, the merchant. Delegated Authentication broker programs are now available from payment networks such as Visa, Mastercard, and GIE Cartes Bancaires.
Customers may have an entirely different purchase experience if you are a larger firm that collaborates with numerous PSPs. Some clients may have even more hassle, or even fewer authentication alternatives, adding further hurdles while completing the transaction. Furthermore, the lack of consistency may do little to alleviate client concerns.
Despite this drawback, delegated authentication has a few benefits. They must be utilized in the following ways:
Provides Control Over The Authentication Process
You already know your consumers, what they want, and the best way to validate their payments without interfering with their experience as an online merchant. Delegated authentication gives you control over the authentication process. You may meet the SCA standards by determining when and how to verify your consumers while ensuring they have a smooth, uninterrupted transaction process.
Encourage Seamless Payments
You must employ Fast Identity Online (FIDO) authentication to join Mastercard and Visa's card scheme programs. The customer account login can be used as payment transaction authentication for merchants registering their customers through the service. FIDO supports passwordless authentication. Thus the consumer only requires their personal device to complete payment. When a consumer decides to make a transaction, they've already verified themselves in an SCA-compliant manner. This is similar to seamless authentication in terms of consumer experience.
Best Practices For Federated Authentication
Federated authentication reimagines user identities and digital service access. An identity provider manages a user's data points to create a single digital identity (IdP). The identity provider develops confidence with other apps and services using a single digital identity.
Federated identity management architecture has significant advantages over traditional authentication solutions. You must utilize these advantages to benefit your company. Listed below are certain factors to keep in mind while doing so:
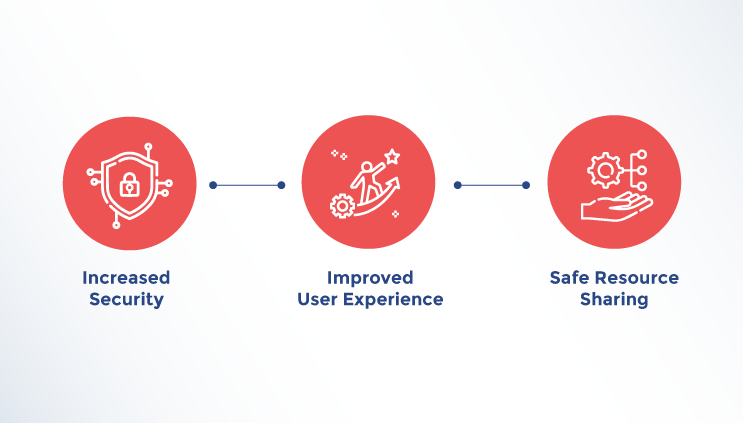
Increased Security
In non-federated systems, a user must log in to each system using a unique set of credentials. Each such login adds a point of vulnerability, increasing the chance of unauthorized people attempting to hack. On the other hand, a Federated identity secures a user's authentication to provide access to apps across many domains. The method also decreases hacking threats by limiting the number of logins to one.
Improved User Experience
Single-point provisioning Federated identity allows for single-point provisioning, making it easier to give users access. Users need to submit their credentials once to access numerous apps across federated domains. This promotes user comfort and productivity while also improving user experiences.
Safe Resource Sharing
Federated companies may exchange information and resources effectively without jeopardizing user credentials or security. Furthermore, data handling is simplified. Organizations utilize an IdP to store user data, which streamlines their data management operations.
Summing It Up
Delegated authentication is preferred in Employee Identity circumstances, such as when current employee credentials must be used for partner or customer portals. However, federated authentication is the more versatile choice and gives a larger technique of linking access management rights. To authenticate user access to common platforms such as Google, federated identity management is used. Despite this benefit, most organizations prefer sing sign on software as it provides access to various systems within the organization, which is generally sufficient. The worldwide economic benefit is that related firms do not have to duplicate information, users are more traceable, and the user experience is enhanced by requiring fewer logins to access numerous services.
So, do not hesitate to purchase an SSO Configuration solution like NinjaAuth by 500apps, which is perfect for enterprises that need to handle various applications with varying authentication requirements. You can add an infinite number of applications and manage them all with a simple and straightforward single sign-on. Visit the 500apps website to learn more about NinjaAuth, one of the best Single Sign On Solution."
Know Why NinjaAuth is the Best for Single Sign-On Solution?
Join the SaaS Revolution
-
All-in-One Suite of 50 apps
-
Unbelievable pricing - â¹999/user
-
24/5 Chat, Phone and Email Support
Infinity Suite
Tags
Email Finder Author Finder Email Validator Email List Email Hunter Email Checker Email Lookup Email Extractor Email Address Finder Email Scraper Find Emails CRM Software CRM Sales CRM CRM Software Enterprise CRM Software Cloud CRM Software Sales Enablement Workflow Automation Retail CRM Call Center CRM Real Estate CRM Sales Tool SDR Software Sales Engagement Platform Sales Qualified Leads Lead Management Tool Sales Tracking Sales Automation Outbound Sales Sales Prospecting Follow Up Leads Lead Management Call Center Software Call Center Software Outbound Call Center Auto Dialer Software Dialer Call Monitoring Automatic Call Distributor Answering Machine Detection Cloud Contact Center Software Virtual Call Center Call Management Time Tracking Time Tracking Employee Monitoring Time Tracker Time Tracking Software Timesheet Employee Time Clock Employee Tracking App Timekeeping Tracking App Time Clock App Applicant Tracking System ATS Applicant Tracking System Application Tracking System Applicant Software Recruiting Software ATS System Applicant Tracking Applicant Tracker Recruitment Software Candidate Relationship Management Systems Video Interviews Assessment Management Recruitment Software Video Interview Virtual Interview Coding Interview Interview Tool Online Assessment Employment Assessment Test Position Management Hiring App HRMS Software Human Resource Management HRMS Software HR Software Payroll Software Human Resource Software Employee Onboarding HRMS HR System Employee Management Document Management AI Writer Lead Enrichment AI Email Writer Sales Pitch Writer AI LinkedIn Outreach SEO Email writer Backlink Email Writer LinkedIn Chrome Extension Opening Line Writer Lead Generation Linkedin Search Prospect Lead Generation Sales Generation Data Enrichment CRM Integrations Technology Search Search with Email Integrations Website Search OKR Tool KPI OKR Task Management Performance Review Employee Performance Evaluation Employee Review Performance Management System OKR Goals MBO Email Notifications Learning Management System LMS Elearning Enterprise Learning Management Professional Development Employee Training Learning Management System Learning Platform Asynchronous Learning Training Management Knowledge Management Chatbot Chatbot AI Chatbot Customer Service Chatbot Online Chatbot Create Chatbot Messenger Chatbot Chatbot Software Website Chatbot Software Survey Bot Bot Builder Help Desk Software Ticketing Tool User Experience Help Desk Software Ticketing System Helpdesk Ticketing System Feedback Management Service Desk Software Support Ticketing Software Helpdesk Support Software Customer Service Ticketing System Live Chat Customer Service Software Live Chat Software Live Chat App Live Chat System Website Live Chat Live Chat Tool Web Chat Software Live Chat Support Software Customer Service Tool Live Chat Service Customer Feedback Customer Feedback Survey Customer Feedback Management Software Feedback Management Tool Customer Satisfaction Survey Software Customer Feedback Management System Client Feedback Software Survey Analysis Feedback Survey Software Feedback Management System User Feedback Software Customer Onboarding Customer Success Management Onboarding Process Workflows Customer Retention Customer Journey Onboarding Checklist User Segmentation Personalization Customized Templates Popup Builder API Platform End To End API Management Unified API Control REST API Management Web API Gateway API Documentation API Management API Integration API Development Unlimited Projects API Gateway Single Sign on Authentication Software Application Management Password Management SSO Configuration SSO Single Sign-On Access Management Easy Set-Up Single Login Secure Login App Builder App Builder Platform Low Code Application Platforms Low Code Development Build Your Own App Low Code App Software Drag And Drop Builder Custom Application Low Code Platform Low Code No Code Bespoke Software App Widgets Custom Widget File Picker Playground OAuth Keys File Manager Website Monitoring Reporting Web Application Monitoring Website Monitoring App Monitoring Performance Monitor App Baseline Analysis Location Insights Alerting System Reporting Wireframe Tool Design UI UX Project Management Mock Designer Wireframe Designer Website Mockup UI Prototyping Image Library Project Management Real-Time Updates Design UI UX Website Builder Website Builder Webpage Builder Website Creator Landing Page Creator Website Maker Blog Builder Ecommerce Website Builder Website Analytics Website Development Landing Page Builder Email Marketing Email Marketing Software Bulk Email Sender Automated Email Email Campaign Systems Email Automation Software Autoresponders Email Blast Service Email Marketing Email Marketing Automation Drip Campaigns Social Media Management Instagram Post Scheduler Social Media Analytics Social Media Management Social Media Planner Social Media Calendar Social Media Scheduling Social Media Listening Social Media Monitoring Social Listening SEO Tool Keyword Tool Link Building SEO Optimizer Website Audit On-Page SEO Broken Link Checker Rank Tracker Website Grader SEO Competitor Analysis Website Recording Website Analytics Click Tracking Usability Testing Website Monitoring Mouse Tracking Visitor Recording Session Replay Conversion Funnels Website Recording Website Visitor Tracker Website Personalization Lead Generation Tool Popup Maker Lead Generation Software Popup Builder Website Personalization Software Lead Capture Software Popup Builder Lead Capture Tool Lead Generation App Website Personalization App Content Planner Content Planner AI Writer Social Media Content Planner Ai Content Writer Social Media Content Calendar Content Generator AI Blog Writer Content Marketing Software Social Media Calendar Social Media Planner Push Notification Push Notification Push Messages Push Notification Service Push Service Push Notification App Custom Notifications Mobile Push Notifications Push Notification For Website Push Notification Tool Push Notification Providers Image Personalization Email Marketing Template Countdown Clock Personalization Software Personalized Software Countdown Clock Countdown Timer In Email Personalization Tool Personalized Images Personalized Videos Conversational Chatbot PPC Management Keyword Research PPC Management PPC Marketing Keyword Finder Keyword Generator Shopping Ads Adwords Reports Keyword Research Tool Keyword Suggestion Tool Team Chat Team Chat Software Collaboration Software Team Collaboration Team Communication Online Collaboration Collaboration Tool Teamwork Collaboration Virtual Communication Team Collaboration Software Business Phone System Virtual Phone Numbers Virtual PBX Toll Free Numbers Business Phone System IVR PBX Small Business Phone System PBX System VoIP Phone Cloud Phone Video Conferencing Video Conferencing Video Call Recording Virtual Conferencing Software Virtual Meetings Virtual Meeting Platforms Virtual Conference Platforms Online Conference Platforms Video Calling Software Cloud Meetings Video Conferencing Software Email Provider Email Software Software For Emails Hosted Emails Email With Domain Custom Email Address Email Hosting Business Email Address Email Encrypted Custom Domain Email Project Management Software Project Management Task Management Project Planner Project Management Tool Task Management Software Project Planning Software Project Management App Task Management App Project Management System Project Management Software Form Builder Form Builder Survey Builder Order Forms Web Forms Form Maker Form Creator Form Designer Survey Maker Survey Creator Custom Form Appointment Scheduling Appointment Scheduling Software Appointment Scheduling System Meetings Scheduler Appointment Scheduling App Online Appointment Scheduling Online Scheduling App Appointment Scheduler Appointment Booking App Calendar Scheduler Online Scheduler Robotic Process Automation RPA Tools RPA RPA Automation Robotic Automation Software Data Scraper Web Scraper Robotic Automation Website Scraper Business Process Automation Robotic Process Automation Business Process Management Workflow Management Business Process Modelling Business Process Automation BPMN BPM Software BPM Tool Business Process Management Workflow Software Workflow Automation Business Process Mapping App Integration Workflow Software Workflow App Workflow Automation Process Automation Application Integration Data Integration Tool Workflow Management Software Data Integration Software Workflow Tool Marketing Automation Electronic Signature Signature Maker Digital Signature Software Digital Signature Pdf Signer Esign Online Signature Signature Creator Sign Documents Online Electronic Sign E Signature
