A Comprehensive Guide to Single Sign on Authentication
Time is a valuable resource. People respond to your efforts by performing better when you save them time. The (SSOA) single sign on authentication function, which offers quick and easy access to services that facilitate corporate activities, is analogous to this concept.

Users can access databases and apps with the aid of single sign on solutions without repeatedly going through several authentication procedures for each one. Users can save time while protecting the security of their assets.
It is unquestionably a crucial component of identity and access management (IAM) in organizations, as users are given a certain set of access privileges.
Now that we have a better understanding of the details, let's examine single sign on authentication in more detail.
All About Single Sign On Authentication
One set of login credentials can be used by a user to log in to a fine array of low code no code platforms and various interfaces that you intend to have collective access into perhaps with different applications, thanks to the single sign on authentication technique that is really effective to simplify this all.
By offering a centralized user authentication service where you don't need to prove your identity repeatedly once you've authenticated, it removes the hassle of remembering complicated usernames and passwords for various services through perhaps a best low code platform to enable activities.
A single sign on should not be confused with the same sign on method, or directory server authentication, which is made possible by the lightweight directory access protocol (LDAP) and server-stored LDAP databases.
The system requires the same login credentials to access each application separately when using directory server authentication. In contrast, for a single sign on, you need to authenticate only once for accessing numerous applications and databases.
A single sign on service provider saves the user's credentials inside and converts them to serve other methods when necessary because different applications utilize different authentication procedures.
Single Sign On Authentication - How It Works
By exchanging certificates with the service provider and identity provider, single sign on verifies users. To guarantee that the details are transmitted from a reliable source, the information is signed on this certificate before being forwarded from the identity supplier to the service provider.
In the (SSOA) single sign on authentication technique, the identification data is transmitted in the form of authentication tokens that include details about the user, including username, email address, and more.
Types of Single Sign On
There are several sorts of (SSOA) single sign on authentication settings. These have as their foundation protocols like Kerberos, Security Assertion Markup Language (SAML), and others.
A ticket-granting ticket (TGT), which is issued in the Kerberos-based configuration once the user provides their login credentials. When accessing other apps, the TGT is used to obtain service tickets, establishing the user's identification without requiring them to be re-entered.
On the other side, SAML is an XML-based technique that enables single sign on by facilitating the exchange of security information between the SAML identity provider and the SAML service provider.
A smart card that contains the user's sign-in information is required for smart card-based authentication. The applications won't ask the user to input their credentials again after the card has been used.

Benefits of Single Sign On Authentication
Regardless of what purpose you access a website for, a seamless experience is always expected with a good custom application development. Nobody likes memorizing separate credentials for accessing sites. With (SSOA) single sign on authentication, these issues can be minimized in a snap, along with various additional benefits.
Improved Productivity
Requests for IT help with logins are a huge time and money waster for everyone involved. A single point of access for several platforms, however, decreases waste and boosts productivity.
Enhanced Security
Users are more inclined to create secure passwords because they only need to remember one set of credentials. As a result, there is less chance that someone will steal your password, protecting the integrated systems.
Additionally, two-factor authentication or multi-factor authentication can increase the security of a single sign on system.
Single Sign On With Risk Based Authentication
(SSOA) single sign on authentication - single sign on solutions enable users to access numerous web-based platforms using a principal ""key."" Some people could find this to be unsafe in terms of security. (SSOA) single sign on authentication can be used in conjunction with risk-based authentication to ensure the security of each entity within the integrated structure (RBA).
You may keep an eye on user activity on each platform using RBA, along with the security team. External identification verification may be required in cases of anomalous user behavior, an incorrect IP address, and repeated login failures. If this verification is unsuccessful, access to the IP address or device will be terminated.
This combination can be quite effective in preventing cyber crimes, including resource drain, site damage, and data theft.

Lesser Password Fatigue
Every website requires a different password in light of the rampant cybercrime rates. This typically requires a mixture of capital and lowercase letters, numerals, and special characters. Password fatigue occurs as a result of having to remember numerous passwords for various websites.
The implementation of an (SSOA) single sign on authentication approach will make it simple for users to access the applications, improving the user experience and reducing password fatigue.
Simplified UX
Any website should prioritize the user experience. Users won't stay on your site no matter how many beautiful features you highlight if the login process is difficult.
You may give your users a cutting-edge digital experience by integrating (SSOA) single sign on authentication. The user will save time with only one-time login needs and less password fatigue.
Shadow IT Deterrence
The term ""shadow IT"" describes the usage of unlicensed software at an organization's expense. This practice was originally restricted to software purchases, but it has rapidly expanded, increasing the risk of identity theft.
Shadow By adopting (SSOA) single sign on authentication, IT can be avoided. This framework allows IT administrators to keep an eye on what their users are doing on company systems, ensuring overall security from cybercrime.
Inclusion of Company Promoted Solutions
Users have an easier time logging into an application when the bother of various login credentials isn't an issue. This is simple to accomplish using (SSOA) single sign on authentication, improving the market and advancing the adoption rate of the applications your business promotes.
Implementation Challenges of Single Sign On Authentication
Although (SSOA) single sign on authentication appears to be the ideal option for the majority of enterprises, there are a few drawbacks that you should be aware of.
Technical Challenges in Integration
The main problem that the majority of businesses have is integrating different systems with single sign on. It’s applicable for both the architecture as well as the security protocols of these systems.
The majority of businesses currently use antiquated ERP or SAP-style systems, which are still far from the current network structure. Modern applications, however, are built using cutting-edge technological architecture.
There must be a center ground for such divergent systems to coordinate seamlessly. It would give each of these systems a common access point and give them single sign on capabilities.
There are several such service providers available right now who offer single sign on capabilities and authorize users who check in on any linked platforms. It should be able to find the user's data in the database, let other programmes know that the user has already logged in, and verify the user's identity.
Every relevant component of the integrated system, such as a mobile application, an online store, a website, a loyalty programme, etc., must support this integration. The difficulty of establishing a smooth (SSOA) single sign on authentication experience is tremendous due to the variety of connectivity points.
Consistency and User Interface
Companies' internal systems can have boring user interfaces. However, when it comes to the authentication procedure, these systems must have a common interface.
By using the same policy and template across all platforms, consistency can be achieved. However, if the projects are built by various teams, comprising devoted product owners and front-end developers, it is difficult to achieve total resemblance in every application. This is due to the fact that each product owner brings their vision to life on the project, resulting in outcomes that deviate from expectations.
When (SSOA) single sign on authentication is implemented, each platform's centrally hosted login page becomes similar. As a result, since logging in will be required for all included systems, the login window will be the same on all customer-facing platforms.
Coordinating Timelines
At least two or more systems are involved in a single sign on framework. It is possible to apply the change in stages, starting with one system and then moving on to the others until the full integration is achieved. Even after splitting the process into stages, there will still be major hurdles.
Due to these difficulties, it is preferable to create and implement (SSOA) single sign on authentication concurrently across all pertinent systems. This will be advantageous for both the business and its customers. By avoiding the chance of repetitive trial-and-error, the company will save a significant amount of time, money, and resources. The consolidated login option will be accessible to users on all platforms.
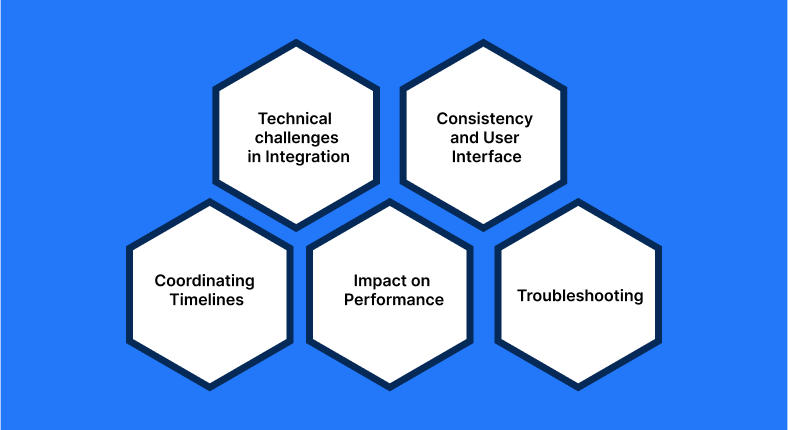
Impact on Performance
The primary mechanism through which the (SSOA) single sign on authentication login procedure operates is a sequence of redirections between the systems and (SSOA) single sign on authentication software. When a user logs in or is automatically logged in owing to checking the “Remember Me” option, the underlying redirection takes a long.
A domain change and redirection to another system or website are to blame for this. The user must wait longer as a result. All users across all systems will experience a delay if the (SSOA) single sign on authentication system even slightly slows down.
There are several potential causes of (SSOA) single sign on authentication slowdown. Consider the case where two channels are used to implement the (SSOA) single sign on authentication solution. These two channels are the only ones that can currently access the (SSOA) single sign on authentication login page. The system is then simultaneously expanded by three more channels. Now, users of five channels can access the (SSOA) single sign on authentication login page. The (SSOA) single sign on authentication system may become slower due to an unexpected surge in traffic, lengthening user delays.
In conclusion, (SSOA) single sign on authentication's performance suffers from its staggered installation. If the login and authorization processes are handled by different systems in this solution, the login time will undoubtedly worsen.
By giving the (SSOA) single sign on authentication system an appropriate and elaborate infrastructure to process the requests effectively and rapidly, this problem can be avoided.
Troubleshooting
(SSOA) single sign on authentication has advantages for an organization, but it also causes certain problems for the people involved. A business must be prepared with a troubleshooting strategy and processes to deal with user concerns before using this structure.
All the systems integrated through an (SSOA) single sign on authentication structure must have specialized support teams. They are tasked with gathering all reported issues and requests and determining where the issue actually began—in the company's system, the (SSOA) single sign on authentication programme, the user end, or somewhere in between. It might be argued that this approach is the most effective way to address all systemic issues.
Top Tools for Single Sign On Authentication
Users who use Single Sign On Software can log in to multiple applications using just one set of login information. Users can move smoothly between applications while IT managers can centralize access management. (SSOA) single sign on authentication's main focus is on enabling safe access to company systems, not on data and password management.
A product must meet the following criteria to be eligible for the list:
To give users access to numerous programmes and databases, use a single portal.
Automate authentication to stop multiple logins.
Access numerous applications with a single authentication server
Provide safe access to information and data
Logins for corporate applications should be integrated.
NinjaAuth - A Single Sign-On Solution
NinjaAuth is a single sign on authentication application that allows users to access multiple applications with a single set of credentials, regardless of where they are hosted, while also assisting administrators in managing access to those applications. With just a few lines of code, you can set up enterprise authentication hassle free. Increase productivity while maintaining data security. For your applications, obtain a secure centralised access management system. A centralized user portal can assist in reducing the app deployment process.
Okta
Okta leverages the power of the cloud to provide identity management solutions like (SSOA) single sign on authentication that integrate directly with an organization's existing directories and identity systems and more than four thousand other applications. It offers an (SSOA) single sign on authentication solution with a full-featured federation engine and flexible access policies.
Citrix Workspace
Citrix Workspace goes beyond conventional (SSOA) single sign on authentication to deliver contextual security and govern app access depending on how and where they are used, assuring increased productivity. It offers a zero-trust method for gaining access to SaaS, virtual, and web applications.
Duo Security
Without sacrificing security, single sign on from Duo Security provides users with a quick and uniform login process for every application, whether it is cloud-based or on-premises. The zero-trust platform interfaces with dozens of different (SSOA) single sign on authentication and identity provider technologies, enabling you to protect access to apps and directories. Duo's cloud-based (SSOA) single sign on authentication complements its multi-factor authentication (MFA) solution.
OneLogin
In order to enable one-click access to all enterprise cloud and on-premise apps across all device types, OneLogin offers quick and secure identity management solutions for businesses. It lowers the cost of identification infrastructure and enables customers to effectively extend identity policies to the cloud.
LastPass
By giving IT superior control and facilitating easy access to apps, LastPass helps businesses be more secure, boost productivity, and maintain compliance. It does this by providing single sign on, password management, and adaptive multi-factor authentication.
Conclusion
The single sign on system can alter how users interact with apps and services, enabling them to produce the outcomes you demand. Introducing single sign on will give them a quick and secure means to access cloud and on-premises applications, enhancing cybersecurity while providing a seamless user experience. To explore more insights into single sign on authentication."
Know Why NinjaAuth is the Best for Single Sign-On Solution?
Join the SaaS Revolution
-
All-in-One Suite of 50 apps
-
Unbelievable pricing - â¹999/user
-
24/5 Chat, Phone and Email Support
Infinity Suite
Tags
Email Finder Author Finder Email Validator Email List Email Hunter Email Checker Email Lookup Email Extractor Email Address Finder Email Scraper Find Emails CRM Software CRM Sales CRM CRM Software Enterprise CRM Software Cloud CRM Software Sales Enablement Workflow Automation Retail CRM Call Center CRM Real Estate CRM Sales Tool SDR Software Sales Engagement Platform Sales Qualified Leads Lead Management Tool Sales Tracking Sales Automation Outbound Sales Sales Prospecting Follow Up Leads Lead Management Call Center Software Call Center Software Outbound Call Center Auto Dialer Software Dialer Call Monitoring Automatic Call Distributor Answering Machine Detection Cloud Contact Center Software Virtual Call Center Call Management Time Tracking Time Tracking Employee Monitoring Time Tracker Time Tracking Software Timesheet Employee Time Clock Employee Tracking App Timekeeping Tracking App Time Clock App Applicant Tracking System ATS Applicant Tracking System Application Tracking System Applicant Software Recruiting Software ATS System Applicant Tracking Applicant Tracker Recruitment Software Candidate Relationship Management Systems Video Interviews Assessment Management Recruitment Software Video Interview Virtual Interview Coding Interview Interview Tool Online Assessment Employment Assessment Test Position Management Hiring App HRMS Software Human Resource Management HRMS Software HR Software Payroll Software Human Resource Software Employee Onboarding HRMS HR System Employee Management Document Management AI Writer Lead Enrichment AI Email Writer Sales Pitch Writer AI LinkedIn Outreach SEO Email writer Backlink Email Writer LinkedIn Chrome Extension Opening Line Writer Lead Generation Linkedin Search Prospect Lead Generation Sales Generation Data Enrichment CRM Integrations Technology Search Search with Email Integrations Website Search OKR Tool KPI OKR Task Management Performance Review Employee Performance Evaluation Employee Review Performance Management System OKR Goals MBO Email Notifications Learning Management System LMS Elearning Enterprise Learning Management Professional Development Employee Training Learning Management System Learning Platform Asynchronous Learning Training Management Knowledge Management Chatbot Chatbot AI Chatbot Customer Service Chatbot Online Chatbot Create Chatbot Messenger Chatbot Chatbot Software Website Chatbot Software Survey Bot Bot Builder Help Desk Software Ticketing Tool User Experience Help Desk Software Ticketing System Helpdesk Ticketing System Feedback Management Service Desk Software Support Ticketing Software Helpdesk Support Software Customer Service Ticketing System Live Chat Customer Service Software Live Chat Software Live Chat App Live Chat System Website Live Chat Live Chat Tool Web Chat Software Live Chat Support Software Customer Service Tool Live Chat Service Customer Feedback Customer Feedback Survey Customer Feedback Management Software Feedback Management Tool Customer Satisfaction Survey Software Customer Feedback Management System Client Feedback Software Survey Analysis Feedback Survey Software Feedback Management System User Feedback Software Customer Onboarding Customer Success Management Onboarding Process Workflows Customer Retention Customer Journey Onboarding Checklist User Segmentation Personalization Customized Templates Popup Builder API Platform End To End API Management Unified API Control REST API Management Web API Gateway API Documentation API Management API Integration API Development Unlimited Projects API Gateway Single Sign on Authentication Software Application Management Password Management SSO Configuration SSO Single Sign-On Access Management Easy Set-Up Single Login Secure Login App Builder App Builder Platform Low Code Application Platforms Low Code Development Build Your Own App Low Code App Software Drag And Drop Builder Custom Application Low Code Platform Low Code No Code Bespoke Software App Widgets Custom Widget File Picker Playground OAuth Keys File Manager Website Monitoring Reporting Web Application Monitoring Website Monitoring App Monitoring Performance Monitor App Baseline Analysis Location Insights Alerting System Reporting Wireframe Tool Design UI UX Project Management Mock Designer Wireframe Designer Website Mockup UI Prototyping Image Library Project Management Real-Time Updates Design UI UX Website Builder Website Builder Webpage Builder Website Creator Landing Page Creator Website Maker Blog Builder Ecommerce Website Builder Website Analytics Website Development Landing Page Builder Email Marketing Email Marketing Software Bulk Email Sender Automated Email Email Campaign Systems Email Automation Software Autoresponders Email Blast Service Email Marketing Email Marketing Automation Drip Campaigns Social Media Management Instagram Post Scheduler Social Media Analytics Social Media Management Social Media Planner Social Media Calendar Social Media Scheduling Social Media Listening Social Media Monitoring Social Listening SEO Tool Keyword Tool Link Building SEO Optimizer Website Audit On-Page SEO Broken Link Checker Rank Tracker Website Grader SEO Competitor Analysis Website Recording Website Analytics Click Tracking Usability Testing Website Monitoring Mouse Tracking Visitor Recording Session Replay Conversion Funnels Website Recording Website Visitor Tracker Website Personalization Lead Generation Tool Popup Maker Lead Generation Software Popup Builder Website Personalization Software Lead Capture Software Popup Builder Lead Capture Tool Lead Generation App Website Personalization App Content Planner Content Planner AI Writer Social Media Content Planner Ai Content Writer Social Media Content Calendar Content Generator AI Blog Writer Content Marketing Software Social Media Calendar Social Media Planner Push Notification Push Notification Push Messages Push Notification Service Push Service Push Notification App Custom Notifications Mobile Push Notifications Push Notification For Website Push Notification Tool Push Notification Providers Image Personalization Email Marketing Template Countdown Clock Personalization Software Personalized Software Countdown Clock Countdown Timer In Email Personalization Tool Personalized Images Personalized Videos Conversational Chatbot PPC Management Keyword Research PPC Management PPC Marketing Keyword Finder Keyword Generator Shopping Ads Adwords Reports Keyword Research Tool Keyword Suggestion Tool Team Chat Team Chat Software Collaboration Software Team Collaboration Team Communication Online Collaboration Collaboration Tool Teamwork Collaboration Virtual Communication Team Collaboration Software Business Phone System Virtual Phone Numbers Virtual PBX Toll Free Numbers Business Phone System IVR PBX Small Business Phone System PBX System VoIP Phone Cloud Phone Video Conferencing Video Conferencing Video Call Recording Virtual Conferencing Software Virtual Meetings Virtual Meeting Platforms Virtual Conference Platforms Online Conference Platforms Video Calling Software Cloud Meetings Video Conferencing Software Email Provider Email Software Software For Emails Hosted Emails Email With Domain Custom Email Address Email Hosting Business Email Address Email Encrypted Custom Domain Email Project Management Software Project Management Task Management Project Planner Project Management Tool Task Management Software Project Planning Software Project Management App Task Management App Project Management System Project Management Software Form Builder Form Builder Survey Builder Order Forms Web Forms Form Maker Form Creator Form Designer Survey Maker Survey Creator Custom Form Appointment Scheduling Appointment Scheduling Software Appointment Scheduling System Meetings Scheduler Appointment Scheduling App Online Appointment Scheduling Online Scheduling App Appointment Scheduler Appointment Booking App Calendar Scheduler Online Scheduler Robotic Process Automation RPA Tools RPA RPA Automation Robotic Automation Software Data Scraper Web Scraper Robotic Automation Website Scraper Business Process Automation Robotic Process Automation Business Process Management Workflow Management Business Process Modelling Business Process Automation BPMN BPM Software BPM Tool Business Process Management Workflow Software Workflow Automation Business Process Mapping App Integration Workflow Software Workflow App Workflow Automation Process Automation Application Integration Data Integration Tool Workflow Management Software Data Integration Software Workflow Tool Marketing Automation Electronic Signature Signature Maker Digital Signature Software Digital Signature Pdf Signer Esign Online Signature Signature Creator Sign Documents Online Electronic Sign E Signature
