Best Practices For Implementing Web-Based Single Sign-On
Business organizations use multiple passwords for professional uses, and their teams use a dozen more for private uses. Security breaches and cyber-attacks have become common because of the vulnerabilities related to passwords. Most risks arise from passwords that are simple, easy to guess, and used in more than one system.
#1
Streamlined Security Compliance
#2
Single Login for Multiple Applications
#3
Easy Deployment of Applications
#4
Improved Control Over Sharing
#5
Combat Password Fatigue
#6
Conditional Access Privilege
#7
Multi-Factor Authentication
#8
Authentication at Ease
#9
Unbelievable pricing - the lowest you will ever find
#10
Everything your business needs - 50 apps, 24/5 support and 99.95% uptime
Employees of an organization waste too much time typing passwords. The best solution for password management is eliminating the use of multiple passwords. You can use a centralized authentication method like a web-based single sign-on system to access all online services. A web-based sign-on system allows you to sign in using a single set of credentials like a unique username and password. The authentication allows you to access multiple password-protected websites and web-based applications.
Best Practices and Tips for Single Sign-On Implementation
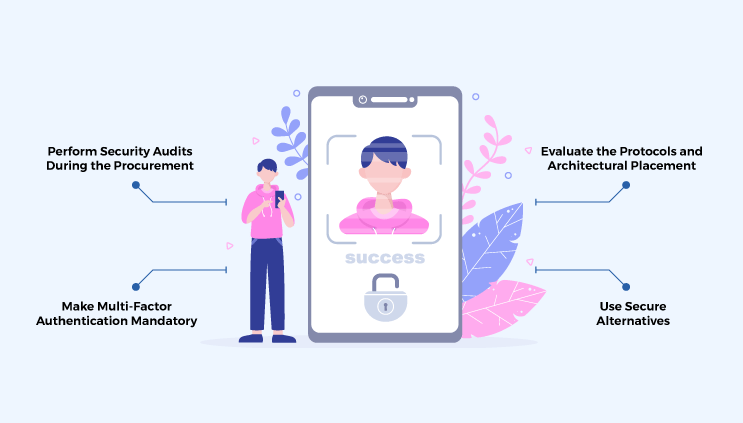
A single sign-on system makes things easier for an organization by enabling a centralized process of authentication and user identity management. However, you must have safeguards in place when implementing SSO in your system. Here is a breakdown of the best practices and tips to implement single sign-on efficiently.
Perform Security Audits During the Procurement
Every organization must focus on procurement standards to ensure the tools have provisioning and de-provisioning facilities during SSO implementation. You must use efficient and trusted tools to make your single sign-on system a powerful one.
Make Multi-Factor Authentication Mandatory
A password-based authentication system must have a second authentication factor to guarantee better security and avoid any incidents of compromise. Organizations must have policies related to password selection and rotation to strengthen the weak links in SSO implementation.
Evaluate the Protocols and Architectural Placement
The location of an SSO protocol in an organization’s IT infrastructure holds significance, and it must meet industry specifications to get implemented. Organizations must ensure that the technology gets properly placed on an authentication stack. It makes sure that the architectural placement of SSO does not mute the original IP address source of the originating user.
Use Secure Alternatives
While setting up SSOs in their systems, organizations should use protocols that make the connections between active systems more secure. These protocols add an extra protection layer when users utilize certificates or security keys while working in the system.
Summing It Up
Authentication processes that use web-based single sign-on systems allow users to access multiple websites, applications, and similar online portals by using a single set of credentials. A centralized authorization and authentication system is the best way for an organization to keep its network secure and increase the productivity of its employees. Thus, SSO implementation helps build a trusted relationship between websites and online systems to ensure the users do not have to bear the pain of remembering multiple passwords every time they sign in to a system. Are you looking for a single sign-on solution for your organization’s system? If yes, you can choose NinjaAuth and boost your system’s productivity by ensuring data security and a centralized access management system at an affordable rate.